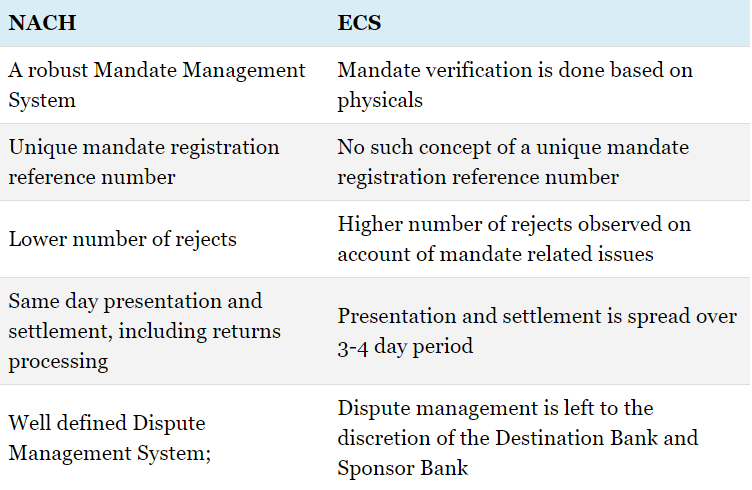
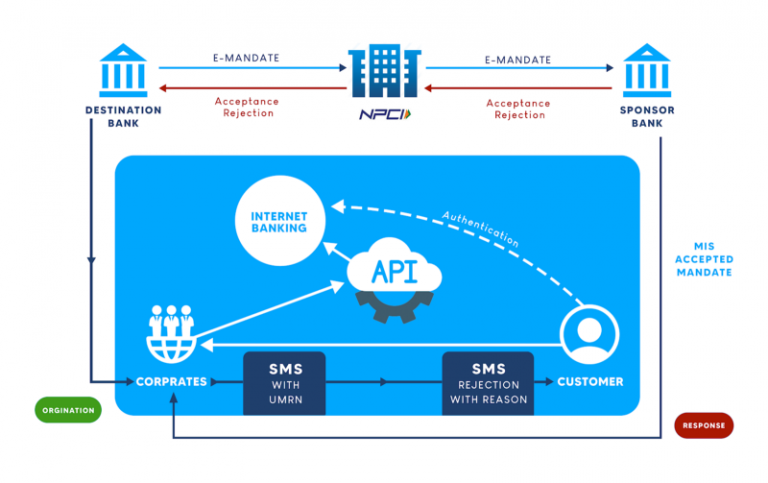
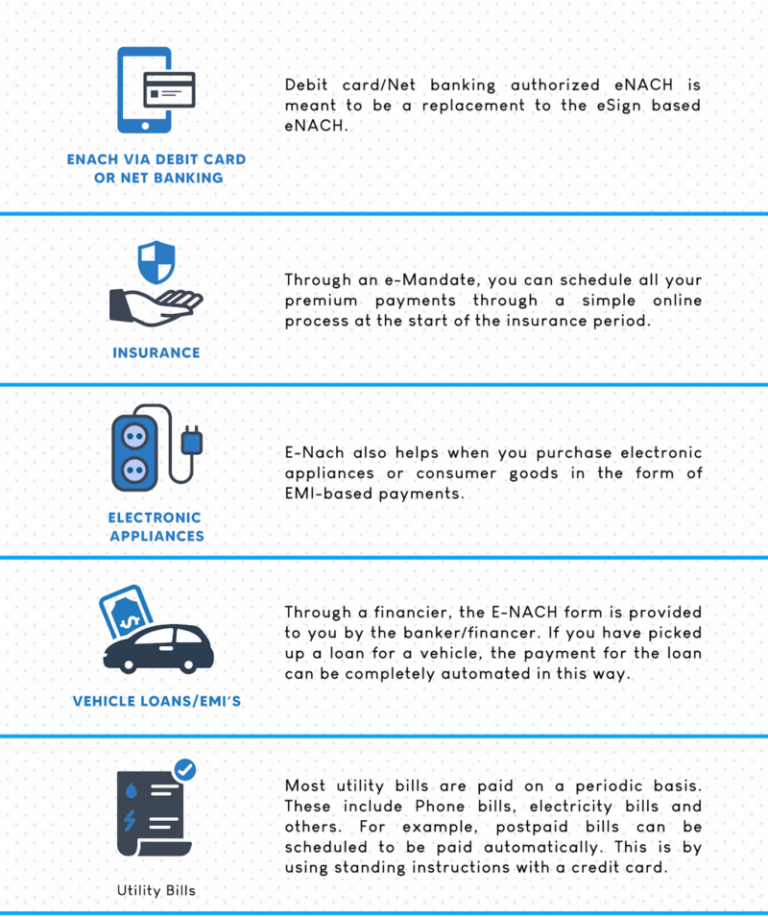
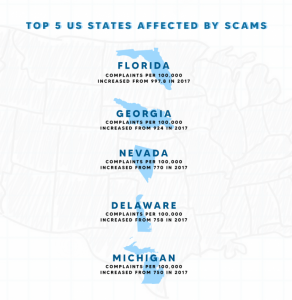
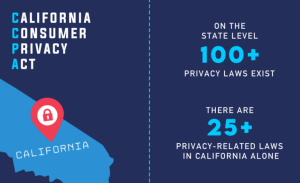
In India, there are many instances in which people choose to rent goods or services for mostly two reasons. Youngsters do not know which city they might have to live in when they relocate for work purposes. Second, many items ranging from clothing to furniture may have a price tag that may not be suitable with one’s income. People who need formal wear for a special occasion may not wish to wait a year to purchase it.
There are other instances as well. There are people who might have transferable jobs and require frequent travel or need to relocate on a yearly basis. Buying a house may not be as prudent a solution as renting it. It is due to these instances that the rental/shared spaces
Rental/Shared Workspace
Starting your own company, or simply relocating to another city for your new job, rental is the way to go. In the last few years, India has seen the rise of startup companies that offer co-working and co-living spaces. They are near each other. Most working professionals or students prefer staying near colleges/schools/workplace.
Some popular co-working companies include WeWork, InstaOffice, GoWork, and Innov8. These offer premium working spaces for developing businesses with a smaller workforce. These office spaces provide premium amenities at pocket-friendly rates like:
1.High-speed Wi-Fi
2. Unique common areas
3. Business-class printers
4. Wellness room
5. Phone booths
6. Meeting rooms
7. Event space
8. Cleaning services
9. Professional & social events
10. Complimentary refreshments
11. Outdoor space
12. Parking
However, the current Covid-19 crisis has changed this equation to a great extent. Most organizations have shifted their employees to the work from home model. In a recent survey conducted by Knight Frank India, reports indicate over 70% of companies sampled for a poll are willing to extend the work for home policy by another six months. A similar trend is emerging globally. Companies worldwide have announced remote working for employees to contain the virus spread. This has triggered a debate if work from home could replace office spaces in the future.
Office utilization rates will fall as remote working increases. Landlords with exposure to short-term leases are the most vulnerable. This is mainly due to the delay to investment activity and softer rental growth than previously forecast with respect to 2020 overall performance, These findings are per JJL’s report titled COVID-19 Global Real Estate Implications.
In 2019, flexible workspaces with 11.2 million sq ft were responsible for 18% share in total leasing. This was according to Colliers International India. Experts suggest that corporates are unwilling to invest in commercial space currently. This will have an adverse effect on shared space providers. With the overall economy in the doldrums and companies/employees getting into the habit of the ‘work from home’ concept, office space is being considered as an additional overhead cost. Many are not willing to invest, at least for the coming two-three quarters.
Rental Accommodation
In 2019, rental living companies have expanded to providing a wide range of services. Living spaces by Zolostay, Nestaway or NoBroker are perfect if you are looking for a place to rent/share.
Some key facts about rental accommodation:
- A December 2018 survey by Knight Frank India shows that 72% of millennials gave co-living spaces a thumbs-up. Over 55% of respondents were in the age bracket of 18–35 years. They were more than willing to rent co-living spaces.
- In a short span, Oyo Living has opened 150 properties with 10,000 beds. Their properties include studio apartments and 1/2/3 bedroom apartments on a shared/private basis. They offer living spaces in Bengaluru, Noida, Pune, and Gurugram. The company is set to expand to the top 10 metropolitan cities with over 50,000 beds.
- In the last four years, NestAway has raised around $94.2 million from marquee investors. The company has over 55,000 tenants living in 25,000 plus homes across 12 cities. It hopes in the next five years, at least a million tenants will call NestAway spaces their homes. The company is set to enter 10 more cities, including Chennai, Kota and Mysore.
- Delhi-based student housing startup Stanza Living manages 2,000 beds mostly in Delhi-NCR. The company plans to have another 10,000 beds that will be launched across cities in the coming months. Stanza is backed by Matrix Partners, Accel Partners and Sequoia Capital,
With the Covid-19 scare hovering above our world, most Indian shared accommodation businesses have come to a standstill. In India, millennials account for 47%, approximately share in the country’’s working-age population, they are an integral target group for coliving spaces.
- With 60% of the students being outstation students, the demand at present stands approximately 100,000 beds across the country for student accommodation.
- Coliving space in India enjoys a worth of 85 Cr INR, approximately. This is responsible for about 2.5% of the entire rental market. This is based on the industry expectation and the forecast which stands at 2X growth in three years.
Before the coronavirus outbreak, government policies were not in place. Shared accommodation, mostly paying guest (PG) facilities were running without definitions. Once the news of Covid-19 took everyone by surprise, the landlords who run PG owners, without giving further notice, asked their tenants to vacate the space with immediate effect.
The reflex from these landlords was a knee-jerk reaction and unfortunate. During such time, people are supposed to be united, but sadly the reality is far distant. However, this could be a boon to the coliving industry. This is because working millennials and students opt for professionally managed accommodation. The co-living operators will see a surge in demand post the Covid-19 days for two reasons. They have firm policies towards safety and hygiene, and hands out a contract to live by — something that was missing in the paying guest format. Safety and hygiene environment will be the critical outlook for the renting of shared accommodations.
Some of the organized players continue to run the space with the booking of 85% of accommodation of total beds, though there is 20%-30% of physical presence. Rest have left to their hometown before the lockdown announcement to be with their family. Experts suggest that the situation will revive post-Covid-19 days.
Need For KYC In Rental Workspace/Accommodation
In modern times, technology is overtaking every sphere of life. Rental companies today are offering remote services for renting office workspace or homes. As such, remote verification for the identity of customers is a must. Digital KYC presents itself as an ideal solution to reduce risks and maximize profitability. Imagine a business environment for PG accommodation. The identities of potential clients are actually ensured before handing them the living space — the true asset of the company. All the risks are properly assessed and background checks are performed to rid the company of any potential legal proceedings.
Rental/Shared Vehicle Industry
- In 2010, with the onset of Ola Cabs in India, hailing a cab became much easier for us. The event marked the onset of a new industry — the vehicle rental industry. In 2013, Uber launched operations in India & the app cabs became quite famous across the nation. and people easily adopted it.
- However as the years have passed, the vehicle rental industry has taken a new turn. With companies like Zoomcar, Revv, Drivezy, Bounce etc, a new chapter began in this sector. Instead of renting cabs at higher prices, people can now rent vehicles like cars or bikes directly without any driver. In a report, Avis mentions that the car rental industry in India is growing at the rate of 35%. It is expected to accelerate further to reach INR 1000 billion by 2022.
- The present COVID-19 crisis has not spared the rental vehicle industry in India. With the lockdown procedures, the rental vehicle economy came to a virtual standstill. Cab-hailing companies such as Uber and Ola have resumed services in certain cities under green and orange zones amid the Covid-19 outbreak. They are likely to have their operations hit significantly even after the lockdown.
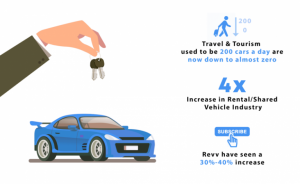
- The Covid-19 crisis has created an aversion to public transport amidst people. As such, self-drive and rental car companies have seen a steep rise in subscriptions and inquiries. Car rental companies like Eco-Rent-a-Car and Revv have seen a sudden spike in demand. Other companies like Zoomcar have witnessed a 4x increase in rentals while some like Drivezy are launching new services to ride the wave. Work from home, fear of infection in public transport, and schools being shut are some of the factors that are contributing to greater demand for car rental companies.
- Currently, the individual cab business for Eco-Rent-a-Car is up to 350 cars a day. However, travel and tourism which used to be 200 cars a day is now down to almost zero.
- Revv have seen a 30%-40% increase in subscription
- Drivezy has slashed the price of the monthly bike subscription to Rs 6,000-Rs 7,000 per month for a duration of 3-months.
- The demand spurt is also leading to markup in the tariff. Self-drive rental Zoom Car has nearly quadrupled its tariffs on self-drive cars in multiple select cities.
So why is KYC necessary?
Rental companies like those in the car rental space can benefit greatly from Digital KYC. It will assist them to authenticate the credentials of their users, before renting out expensive vehicles. This will not only lead to greater transparency but also would reduce the risk of auto theft for car rentals. The danger of Identity thefts and use of fake IDs can be minimised with KYC advantages like fraud management, background checks would lead to streamlined business operations..
Rental Consumer Goods
Moving to a new place but cannot afford new furniture? Companies like Rentomojo, Furlenco and Quickr will help you get rental furniture at affordable prices. Anything you can imagine you need but can’t buy, you can find on rent today.
- According to a report by PricewaterhouseCoopers, the sharing economy is set to generate potential revenue of $335 billion by 2025 globally.
- In 2019, the rental industry has made a huge market in India with estimates that the market stands at about $1.5 billion.
- In an article by Livemint, a rough estimate shows that the market for rental of furniture is seen at around $800–850 million. Rentals of electronic appliances are approximately a market of $500 million while that of bikes is $300 million.
KYC As A Benefit
The need for KYC in the rental goods market is just like all the examples mentioned above. In fact, there are many companies like Furlenco, GrabOnRent which have already started to adopt the online KYC process. Most rental goods companies operate via the Internet and the business model is set up in such a way that the tenant never has to meet the seller. Other than security issues, knowing the customer is important considering most users pay online for their rentals. Rental/shared economy operates on a large customer base. To maintain customer data, KYC collection and verification is required.
DigitalKYC By Signzy For The Rental Market
Digital KYC has been a huge success in the banking industry. In recent years, most Indian regulators have also accepted the use of VideoKYC to secure banking and financial services in terms of onboarding new customers. With social distancing and remote digital services becoming the norms for all businesses, it is only a matter of time before digital KYC collection becomes the standard for all business sectors
With the new government regulations and the current Covid-19 crisis, , electronic KYC collection is now an easy option for rental companies. At Signzy, we offer a unique e-KYC solution known as RealKYC. The solution offers KYC collection as well as background verification and checks.
Signzy provides 2 unique digital KYC solutions with its proprietary AI technology — RealKYC & VideoKYC. Here are some benefits of using Digital KYC for rental businesses:
Advantages of RealKYC & VideoKYC
- Secure System: A customer’s account information during rental onboarding are secure because the entire process is online. Identity theft, fraud, etc. are all minimized with RealKYC.
- Pre-Filled Forms: Real-time data pre-population from uploaded ID proof eliminates the need for manual form filling for the customer during signup on the rental platform.
- Real-Time Document Verification: This can be used to effectively verify KYC documents without the need to wait for an indefinite period. This may be crucial to services like rental accommodation where the customer may need to avail the service on an immediate basis.
- Faster processing: The VideoKYC service is completely automated online. This means that KYC data can be processed in real-time without any manual intervention. The paper-based KYC process can take days up to weeks to get verified, but the VideoKYC process takes just a few minutes to verify and issue.
- Efficient Maintenance For Records: The VideoKYC service by Signzy features collecting time-stamps and keeping an audit trail. This can help businesses maintain track on customers in terms of when the rent/subscription period starts.
Conclusion
The future looks bright for the rental companies looking to expand across India. But the need for effective management of their customer base is also a burning need. Like banks, KYC is the best way to, as the term suggests, ‘Know Your Customer”. These companies will soon have to look towards a more digital approach towards KYC collection and verification
With rental/economy growing at such a fast pace, the companies that operate rental goods/services may need to reconsider their current approach and go for a more structured business model that can effectively manage a large consumer base.
About Signzy
Signzy is a market-leading platform redefining the speed, accuracy, and experience of how financial institutions are onboarding customers and businesses – using the digital medium. The company’s award-winning no-code GO platform delivers seamless, end-to-end, and multi-channel onboarding journeys while offering customizable workflows. In addition, it gives these players access to an aggregated marketplace of 240+ bespoke APIs that can be easily added to any workflow with simple widgets.
Signzy is enabling ten million+ end customer and business onboarding every month at a success rate of 99% while reducing the speed to market from 6 months to 3-4 weeks. It works with over 240+ FIs globally, including the 4 largest banks in India, a Top 3 acquiring Bank in the US, and has a robust global partnership with Mastercard and Microsoft. The company’s product team is based out of Bengaluru and has a strong presence in Mumbai, New York, and Dubai.
Visit www.signzy.com for more information about us.
You can reach out to our team at reachout@signzy.com
Written By:
Signzy
Written by an insightful Signzian intent on learning and sharing knowledge.


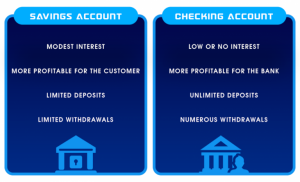
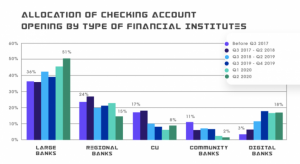
 Source- CORNERSTONE ADVISORS
Source- CORNERSTONE ADVISORS