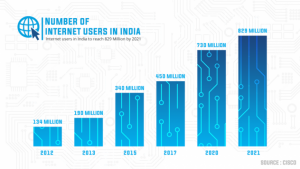
Last year Forbes reported that 2% to 5% of the world’s GDP is laundered every year. This estimates to an amount between $800 billion and $2 trillion. The astounding fact about the report was that only 10% of the laundered money is detected, implying more than 90% of the laundered money is unknown to most regulatory bodies and financial institutions.
Money laundering is a major issue in the world. Governments are striving to find newer methods to tackle it. Most financial institutions and companies are accustomed to traditional methods for preventing money laundering. These include in-person verification or traditional automation.
But with the advent of advanced technologies like AI and Machine Learning, they have to adapt for better results. The latest technology integrated Suspicious Activity Reports(SARs) caused more than 31% of laundered money to be blocked.
Thus the need for technology in preventing money laundering is not a matter of if, but when. But how do we do it? What technological tool can we use? Here comes Application Programming Interfaces(APIs) for the financial industry. This article explores what AML screening solutions APIs are and how they can help in preventing money laundering.
Why Is AML Essential In The Financial Industry?
Anti-Money Laundering includes all measures taken by authorities, institutions and individuals to prevent financial criminals from disguising and hiding illegally obtained money as legitimate income. It is essential as money laundering is a financial crime that affects the economy on a microscale as well as momentous levels. The methods of money laundering are transforming with the development of technology. It is only essential that AML screening solutions up their game too.
In July 1989, many nations came together to form the Financial Action Task Force(FATF). The summit was held in Paris and aimed at analysing laundering risks and preventing them with AML measures and AML screening solutions. But after the 9/11 attacks, in October 2001 the FATF updated their agenda and mission to include modes to stop terrorist funding through money laundering. AML procedures have been made better through the decades since.
The European Union also acknowledged and implemented the first AML directive in 1990. It prevented using the flaws in the financial system for laundering. Now The Union is one of the pioneers in revising and upgrading AML measures to reduce risk and terrorist funding. The International Monetary Fund(IMF) with its 189 member states also takes initiatives for AML with compliance measures for financial institutions. Thus all governments are forced to ensure compliance and all institutions are expected to follow suit.
In 2019 the US State Department published a report stating general AML measures succeeded only 0.2% because of non-compliance and inefficient processes. More than 85% of the 11500 companies evaluated in the US were not AML compliant. 2019 also saw AML non-compliant banks paying more than $6.2 Billion in fines globally.
What Is The AML Process And Why Is Compliance Important?
Government bodies and other regulators provide guidelines and procedures that companies and financial institutions can follow to prevent money laundering.
- One of the most important and effective processes is Know Your Customer(KYC). KYC ensures that companies know who their customer is by verifying his financial data with pre-existing credible databases. This way any suspicious activity by the customer can be red-flagged easily.
- Customer Due Diligence(CDD) is also a relevant procedure for AML. Companies evaluate the risk involved with each customer and take necessary measures. This is the process of CDD. They categorize customers as low, moderate or high risk. For example, a Politically Exposed Person(PEP) falls under the high-risk umbrella.
- Another measure is setting a limit for transactions to be monitored. For example, in the US any transaction of more than $10,000 is reported by the institution to the authorities for monitoring. Each country has such a limit to detect any massive fraud. Thus, monitoring and reviewing customer transactions without compromising privacy is very important to prevent AML. If any suspicious activity is detected, then an activity report is generated and transferred to the Compliance and Risk Department.
It is of incredible significance that financial companies follow all the regulatory compliance guidelines for AML. Even a single discrepancy can result in dangerous repercussions. Money Laundering is no longer just for the money. It can even be used as a wrench in the equilibrium of world peace. Besides this, if companies don’t comply they are charged heavy fines by regulatory bodies. AML fines amounted to $4.27 billion in 2018 which nearly doubled in 2019 to $8 billion. This is a collective effort and even the smallest of the financial institutions need to play their part well by following the compliance guidelines.
How Are APIs Used To Help Prevent Money Laundering?
Software connections between computer programs or even computers are called Application Programming Interfaces(APIs). It offers services to other software once it is integrated into a working system. It can be grossly described as an intermediary software that helps other applications communicate among themselves. They are used in almost all companies with a demand for any form of software technology.
AML screening solution APIs are taking over not just the financial sector, but any industry interested in innovative automation. This is because APIs offer agility and more importantly scalability for companies. Recently, after several government policy amendments, APIs are starting to play crucial roles in AML and KYC compliance. This is because the verification of tens of thousands of customers is not practical with traditional processes.
APIs are used for almost all forms of innovative verification procedures. It ensures that processing is efficient without human error. Since it can be replicated on a large scale, it becomes commercially viable. In addition to this most APIs can be procured at affordable prices. Hence, be it a large bank or a small financial institution, automation is simple and inexpensive. APIs help all businesses Combat Financial Terrorism(CFT) at a modest price.
They are in high demand among elite institutions because they offer swifter and inexpensive methods to ensure services meeting customer demands. Since they are adaptable and customizable, they do get an advantage of future-proofing. In the Financial category alone, more than 2000 types of APIs are used across the globe. This will exponentially grow with advancements in AI, Machine Learning and Blockchain technology.
APIs In AML And Regulatory Compliance
Improved user-friendly APIs are available in the industry now. But it needs to fulfil another crucial criterion for integration into any service or product- Regulatory Compliance. Across the world, there are numerous regulatory guidelines for financial institutions. A good example is the PSD2 changes in Europe. Not only are companies encouraged to accomplish more with AML screening solutions and related technologies, but are fined for any lack of compliance on their part.
Financial Institutions that wait and observe if the new technology trends will be left behind in the race. The most adaptable companies will flourish in the long run. Traditional modes of in-person verification processes and human error packed execution are outdated. APIs can automate almost the entire processes saving companies time and money. On an estimate, more than $500 million is spent by financial institutions for financial crime prevention and compliance requirements.
What Are The Benefits Of Using APIs For AML?
APIs do not merely automate the AML and regulatory processes. They enhance them. There are numerous benefits associated with using APIs for AML and verification processes. They include:
- TAT is reduced resulting in quicker processing and better customer journey.
- Near zero human error
- The extremely customizable nature of APIs makes integration easy.
- Inexpensive in the long term.
- The human workforce can focus on discrepancies rather than regular workflow, increasing efficiency.
- Eliminates all storage spaces as all documentation will be in soft copies.
- The better customer onboarding experience
- Better user interface
How Can Signzy Help You?
We offer numerous services, products and AML screening solutions APIs that are useful for your ventures. We Make sure that they are state of the art, because we do not compromise quality. Signzy’s quiver of APIs and associated products are incredibly customizable. You can select which specific APIs suit your requirement and then integrate them into the required systems.
With over 240+ microservice APIs alone, the collection is diverse and versatile. All of our products meet regulatory compliance standards without compromise. But we make sure that the user would not be troubled with inefficient customer journeys. Our systems are efficient and seamless rendering the user experience truly satisfying.
With advancing technology financial institutions and companies deem change. If you do not opt for the right changes, the entire entity’s progress would decelerate. That’s why we at Signzy ensure that you get that which suits your needs. We can make your customer’s journeys easy while making your aspirations easier.
About Signzy
Signzy is a market-leading platform redefining the speed, accuracy, and experience of how financial institutions are onboarding customers and businesses – using the digital medium. The company’s award-winning no-code GO platform delivers seamless, end-to-end, and multi-channel onboarding journeys while offering customizable workflows. In addition, it gives these players access to an aggregated marketplace of 240+ bespoke APIs that can be easily added to any workflow with simple widgets.
Signzy is enabling ten million+ end customer and business onboarding every month at a success rate of 99% while reducing the speed to market from 6 months to 3-4 weeks. It works with over 240+ FIs globally, including the 4 largest banks in India, a Top 3 acquiring Bank in the US, and has a robust global partnership with Mastercard and Microsoft. The company’s product team is based out of Bengaluru and has a strong presence in Mumbai, New York, and Dubai.
Visit www.signzy.com for more information about us.
You can reach out to our team at reachout@signzy.com
Written By:
Signzy
Written by an insightful Signzian intent on learning and sharing knowledge.