About 85 countries in the world have their data privacy policies in place. Sadly, India isn’t one of them. While the Information Technology Act, 2000 does touch upon privacy policies, it’s hardly sufficient. The countries that have data privacy regimes are also evolving their models to suit the BIG DATA wave. For example, in the US, where user data privacy is protected under a bunch of legislations like the Children’s Online Privacy Protection Act, the Gramm-Leach-Bliley Act for financial information, the California Online Privacy Protection Act in California, etc is still looking for more a better way to regulate.
Comparing the US, the framework with the one from EU, Michelle De Mooy, the director for privacy and data at the Center for Democracy & Technology, explains that Europe has a “people-first mentality” that’s ”more than we do here in our capitalist society, where innovation is sort of equated with letting businesses do whatever they need to grow. That has translated into pretty weak data protection.”
EU is tightening its laws further with the upcoming GDPR. It has already got companies hustling to making their privacy policies compliant with the new laws. As the world gears up for a more stringent GDPR, let’s look at how Indian banks and financial institutions can approach data privacy despite the lack of regulations.
Failing on the data privacy score
Most banks and financial companies are committed to maintaining their data integrity and protect it against breaches. However, the same isn’t true when it comes to ensuring security & privacy. You could say that there’s some degree of laxity. Blame it on the “largely self-regulated” privacy guidelines or the “depends-on-the-context” grounds, but banks and financial institutions offering both data security and privacy are few.
In a global survey of more than 180 senior data privacy and security professionals, Capgemini found that lesser than 29% of them “offered both strong data privacy practices and a sound security strategy.”
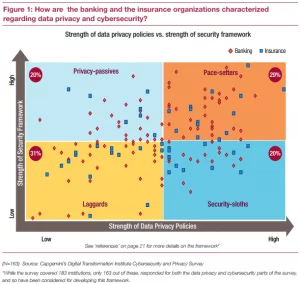
What makes the situation more serious is that today’s banks use a giant tech ecosystem with partners sharing data to build better digital experiences for the end users. As data exchanges hands and lives in multiple places, the risk of data privacy breaches increases. This calls for an even more robust and thorough data privacy regime applying to the entire banking and fintech ecosystem.
But without much legal guidance on approaching data privacy, banks and financial institutions too are forced to take the self-regulation route just like the cryptocurrency businesses. Here’s how banks can handle data privacy until the regime gets regulated.
Self-regulation
While the data privacy laws are ever-evolving, some best and practice data privacy practices can prepare banks and financial institutions for the time when the laws and policies are actually formulated. PwC offers 6 excellent action points for financial institutions to use when handling data privacy:
- Define privacy as primarily a legal and compliance regulatory matter.
- Create a privacy office that develops privacy guidelines and interfaces with other stakeholders. If the financial institution does not currently have a separate privacy office, we recommend for the institution to hold an internal “privacy summit” that convenes key stakeholders from the lines of business, technology, compliance, and legal.
- Identify and understand what the data is, where it resides, how it is classified, and how it flows through various systems. For example, financial, medical, and PII are subject to different restrictions in different jurisdictions.
- Develop appropriate global data-transfer agreements for PII and other data that falls under privacy requirements.
- Recognize and adhere to requirements when developing core business processes and cross-border data flows.
- Preserve customer trust as the primary goal.
McKinsey & Company recommend another great tactic for approaching data privacy that companies can adopt to become data stewards. This strategy is of creating a “golden record” of every personal-data processing activity in a company to ensure compliance and traceability that goes “beyond documenting the system inventory and involves maintaining a full record of where all personal data comes from, what is done with them, what the lawful grounds for processing are, and whom the data are shared with.“
This tactic applies seamlessly to banks and financial institutions. They can start off by building records of what data they collect from their users and how the sharing with their tech partners happens — all of this while ensuring users’ consent for all their operations using the data.
In fact, in addition to self-regulating the data collection, usage, and sharing regime, banks must also build a data privacy taskforce that’s committed to ensuring compliance with the internal data privacy framework.
With the right records, resources, banks, and financial institutions must also see how they can ensure data privacy into their services and offerings by design and by default.
At Signzy, we don’t just view user data privacy proactiveness as a risk management strategy, but we see it as a core building block of a digital trust system. It’s a competitive advantage. We believe that data privacy inspires trust. And when we build digital solutions to tackle challenging legacy financial processes, we make sure that our solutions are structured in a way that user data privacy isn’t compromised while balancing both user expectations and regulatory compliance.
Wrapping it up
Although privacy is a largely law-regulated — and we currently lack the laws — it’s still not optional. And it goes way beyond just seeking the users’ consent for collecting and storing the information. While banks and financial institutions can’t probably go so far as to give their users the “right to erasure” or the “right to be forgotten,” they can surely embrace data privacy as the norm. With stringent self-regulation measures, Indian banks and financial companies can contribute to building trust and transparency in the Indian digital banking scenario until the laws get formulated.
About Signzy
Signzy is a market-leading platform redefining the speed, accuracy, and experience of how financial institutions are onboarding customers and businesses – using the digital medium. The company’s award-winning no-code GO platform delivers seamless, end-to-end, and multi-channel onboarding journeys while offering customizable workflows. In addition, it gives these players access to an aggregated marketplace of 240+ bespoke APIs that can be easily added to any workflow with simple widgets.
Signzy is enabling ten million+ end customer and business onboarding every month at a success rate of 99% while reducing the speed to market from 6 months to 3-4 weeks. It works with over 240+ FIs globally, including the 4 largest banks in India, a Top 3 acquiring Bank in the US, and has a robust global partnership with Mastercard and Microsoft. The company’s product team is based out of Bengaluru and has a strong presence in Mumbai, New York, and Dubai.
Visit www.signzy.com for more information about us.
You can reach out to our team at reachout@signzy.com
Written By:
Signzy
Written by an insightful Signzian intent on learning and sharing knowledge.