Introduction
At Signzy we ensure that building a web application from scratch must be integrated with Security measures. Security first is always our primary motive hence starting with the developer journey till delivery to the customer we ensure that every cycle of development gets processed through rigorous security measures. This post will help us to know how we at Signzy are making millions of onboarding Secure through our platform.
Encryption Methodology
Signzy’s Merchant Onboarding platform communications take place over the TLS 1.2 channel which ensures the encryption of the data in transit during the execution of the product API microservices. TLS uses both asymmetric encryption and symmetric encryption along with the process of TLS handshake which ensures that no stone is unturned during the secure transmission of data during transit.
TLS is a cryptographic protocol that provides end-to-end security of data sent between applications over the Internet and is used as a standard worldwide. The TLS protocol is designed to provide three essential services to all applications running above it: encryption, authentication, and data integrity.
Apart from the data which is passing in transit, we ensure that the data which is residing at rest is also being stored in the encrypted form. Data at rest uses Disk level encryption methodology which ensures the Confidentiality & Integrity of the data at all times.
Penetration Testing
Exhaustive Manual & Automated Penetration Testing is one of the key areas in which our Information Security team is aligned to. Monthly assessments of our product & platform as per the OWASP Top 10 standards & techniques are being performed. Our dedicated security team aims to bring out more Business Logic flaws to ensure that no attacker can exploit the same. We use Licensed BurpSuite Professional in order to test the web applications & other native Android & iOS applications as well.
At Signzy we also ensure to provide our clients & customer base with a dedicated 3rd party CERT-IN Vendor Penetration Testing reports which create a firm assurance that the security of the Signzy Platform is up to the mark. All the vulnerabilities are being tracked as per the standard SLA.
DevSecOps – Developer Security Operations
Integrating Security into the platform from the very first stage of development till the delivery of the product is what DevSecOps Cycle is all about. At Signzy we have ensured that all the development that takes place undergoes the devsecops cycle to ensure the maximum integration of security & knowing about the misses in the early stage of the product development cycle. In each phase of the DevOps cycle starting right from planning to release we ensure that sufficient measures are in place to detect, monitor & fix the issues before the release of the Product.
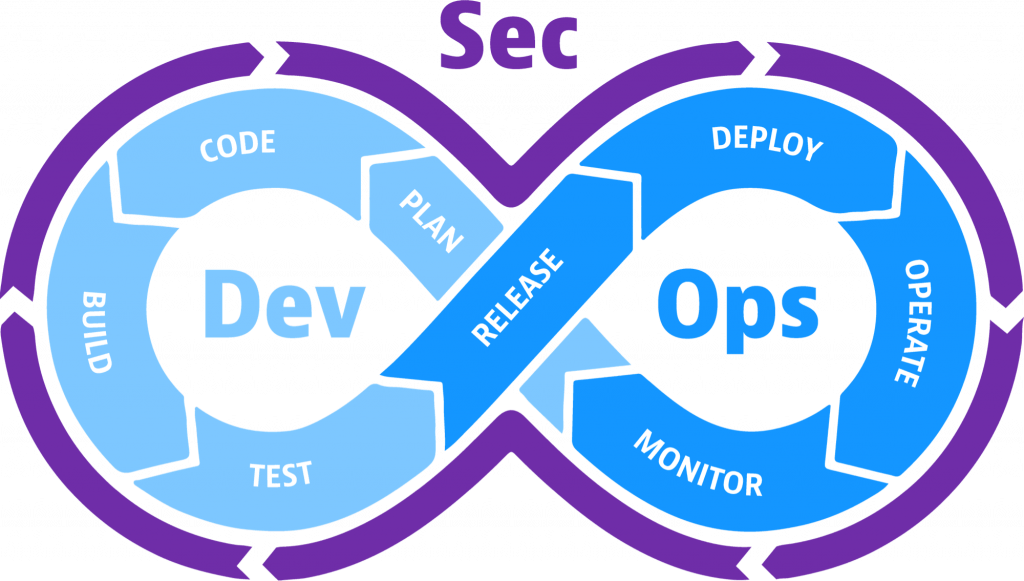
SAST – Static Application Security Testing
SAST is another area where the Information Security team of Signzy is digging into the source codes & making them secure on a periodic basis. Source Code security is one the most crucial things for which we have adopted the approach of both manual & automated security testing. Signzy’s Security team members look out for issues as per the OWASP standards to eliminate the issues prevailing in source codes. Signzy has onboarded Checkmarx Enterprise to ensure the automated security testing of source codes on every release of the products.
Other measures for Application-Level Security:
Apart from the above practices that we follow, there are some other measures as well which we ensure to have in place:
- IP based whitelisting Mechanism
- Role-Based Access Controls for different user role privileges.
- Technologies to monitor exceptions, logs, and detect anomalies in our applications & infrastructure.
- Upgrading dependencies and making sure none of them have known vulnerabilities.
End of the post.
Signzy Information Security Team can be reached at: