Key Highlights
Key Highlights- More than 1.1 million identity theft reports were filed in 2022 through the FTC’s IdentityTheft.gov.
- Consumers lost over $10 billion to fraud in 2023, the highest reported amount ever.
- 22% of U.S. adults, or over 24 million households, have fallen victim to account takeover fraud.
Most people imagine identity thieves as mysterious hackers in dark rooms, targeting strangers through sophisticated computer attacks.
Yet the most common identity theft cases start with something as simple as a misplaced wallet, a wrong website visit, or a routine phone call from someone claiming to be your bank.
There are endless such everyday actions which fraudsters can exploit to fraud you.
However, just as every lock has a key, every scheme has its telltale signs.
And here’s what fraudsters don’t want you to know: their methods are simple, consistent, and – once you know what to look for – surprisingly easy to spot.
If you’ve got 6 something minutes, below are 7 common types of identity frauds with their obvious-but-often-missed signs.
And yes, we are covering their specific solutions as well.
What Is Identity Fraud?
Identity fraud happens when someone steals and uses your business information for their gain.
Think of your business identity like a digital fingerprint – it includes everything from your tax ID and credit accounts to your business licenses and banking relationships.
In present times, identity frauds rarely follow the old smash-and-grab pattern.
Instead, it often unfolds slowly and methodically, with criminals taking time to study business patterns before striking, making it more dangerous.
However, the earlier you spot, the less dangerous it becomes. Let’s examine the seven most common types of identity theft targeting businesses today.
1. Business Financial Identity Theft
Business financial identity theft operates with remarkable subtlety (nothing near to those hollywood-style heists), often detected only after significant damage occurs.
The method is methodical: criminals target business credentials, then systematically exploit them across multiple financial channels.
The primary targets include:
- Business credit systems and supplier payment networks
- Banking relationships and loan application processes
Business Financial Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Unexpected dips in business credit scores |  High High |
Set up daily credit monitoring with alerts. |
| Unfamiliar credit applications |  High High |
Lock business credit files with bureaus. |
| Vendors reporting missing payments you show as paid |  High High |
Implement dual-control for payments. |
| Unknown new credit accounts |  High High |
Regularly check business credit reports. |
| Unexplained bank account charges |  High High |
Set up bank activity monitoring. |
2. Synthetic Identity Theft
Synthetic identity theft works like this: criminals take real pieces of your business information – perhaps your tax ID number – and combine it with false details to create a new, fake business identity.
Then they use this hybrid identity to open accounts, secure credit, or conduct fraudulent business deals.
What makes it particularly dangerous is that these synthetic identities contain enough real information to pass initial security checks. The criminal might use your actual business address but a slightly modified company name, or your tax ID with different owner details.
Synthetic Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Unknown business affiliations appearing |  High High |
Verify all business relationships. |
| Unfamiliar credit inquiries |  High High |
Freeze credit with major bureaus. |
| Duplicate tax ID usage alerts |  High High |
Use a tax ID monitoring service. |
| Mysterious vendor accounts |  Medium Medium |
Implement multi-step verification for vendors. |
| Business mail going to unknown addresses |  Medium Medium |
Set up address verification for mail. |
 Related Blog: What is Identity Theft?
Related Blog: What is Identity Theft?3. Medical Business Identity Theft
Businesses providing employee healthcare benefits are particularly vulnerable to this fraud.
The fallout can devastate a business on multiple fronts:
- State medical privacy law breaches
- Corrupted medical histories
- Mixed medical records with fraudulent claims
- Personal liability concerns for affected staff
- Unexpected billing disputes and resolution costs
- Legal fees for regulatory compliance issues
Usually, it occurs when someone uses your business information to submit false insurance claims or obtain medical services. According to healthcare security reports, this type of fraud often involves a sophisticated understanding of medical billing systems and insurance processes.
Often, they bill for services never rendered, submit false claims, or use your employees’ health insurance information.
Medical Business Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Unexpected insurance claims |  High High |
Contact your insurer to verify claims. |
| Unknown medical charges |  High High |
Dispute charges with providers. |
| Provider number misuse |  High High |
Suspend and reissue your provider number. |
| Benefits maxed out unexpectedly |  Medium Medium |
Report to benefits provider and review history. |
| Unfamiliar patient records |  High High |
Verify records with your medical office. |
4. Account Takeover Fraud
Account takeover fraud means exactly what it sounds like. Someone gains control of your business accounts. But here’s the important part – they don’t just break in and start moving money.
These criminals often quietly observe your normal business patterns first, learning how to mimic your regular transactions to avoid detection.
The dark web has made this type of fraud more sophisticated. Criminals can buy stolen business credentials and use them to access everything from your banking portals to your supplier accounts.
Account Takeover Fraud Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Failed login attempts from new locations |  High High |
Enable location-based authentication. |
| Password reset requests you didn’t make |  High High |
Use multi-factor authentication. |
| Changed account settings or preferences |  High High |
Enable notifications for account changes. |
| Unusual transaction patterns |  Medium Medium |
Monitor transactions in real time. |
| New users added without authorization |  High High |
Implement a user access audit system. |
5. Tax Identity Theft
Tax identity theft hits businesses where it really counts – right in the tax records. Key risk areas include:
- Tax ID numbers exposed in data breaches
- Compromised tax preparation service accounts
What does this mean? Someone uses your business information to file fraudulent tax returns or claim refunds that belong to your company.
The first sign often comes as an unwelcome surprise: the IRS rejects your legitimate tax filing because “you’ve already filed.”
The costs run deeper than just lost refunds. Sorting out tax identity theft means hours with tax authorities, reconstructing records, and potentially delayed tax benefits that your business needs for operations.
Tax Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Rejected tax returns (already filed) |  High High |
Contact the IRS to resolve and verify filings. |
| IRS notices about unknown filings |  High High |
Request an IRS Identity Protection PIN. |
| Multiple tax returns under your EIN |  High High |
Get IRS transcripts and report the issue. |
| Unknown reported income |  Medium Medium |
Review and report discrepancies to the IRS. |
| Unexpected tax payment demands |  Medium Medium |
Contact the IRS and your bank to verify. |
6. Document Identity Theft
Imagine criminals are creating, stealing, or altering your core business documents. Think company formation papers, licenses, and certifications.
In short, Document identity theft is when fraudsters are attacking your business’s legal identity.
Why do criminals target these documents?
Because authentic-looking business documents open doors to bigger frauds: large purchases on credit, business loans, or government contracts. One altered document can multiply into a chain of fraud that takes months or years to untangle.
Document Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Unknown business filings |  High High |
Verify with the business registration agency. |
| Duplicate business licenses |  High High |
Report to local authorities and request a new license. |
| Modified certification documents |  High High |
Contact certifying body to verify authenticity. |
| Unfamiliar business locations listed |  Medium Medium |
Cross-check with your records and notify authorities. |
| Unknown officers on business records |  High High |
Verify with the state registry and update records. |
7. Biometric Identity Theft
Biometric identity theft represents the newest frontier in business security threats.
As more companies adopt fingerprint scans, facial recognition, and other biometric security measures, criminals have found ways to capture and replicate this data.
Unlike passwords or PINs, you can’t simply change your fingerprints or facial features after they’ve been compromised.
Once stolen, biometric data remains vulnerable indefinitely.
Biometric Identity Theft – Risk Profile and Specific Solutions
| Warning Sign | Risk Severity | How to protect yourself |
| Failed biometric authentications |  High High |
Use backup authentication methods and re-enroll biometrics. |
| Unauthorized access attempts |  High High |
Reset security protocols and block unauthorized access. |
| System flags duplicate biometrics |  High High |
Re-enroll and tighten security. |
| Unusual verification patterns |  Medium Medium |
Set alerts for suspicious activities. |
| Multiple registration attempts |  Medium Medium |
Limit registration attempts and add verification steps. |
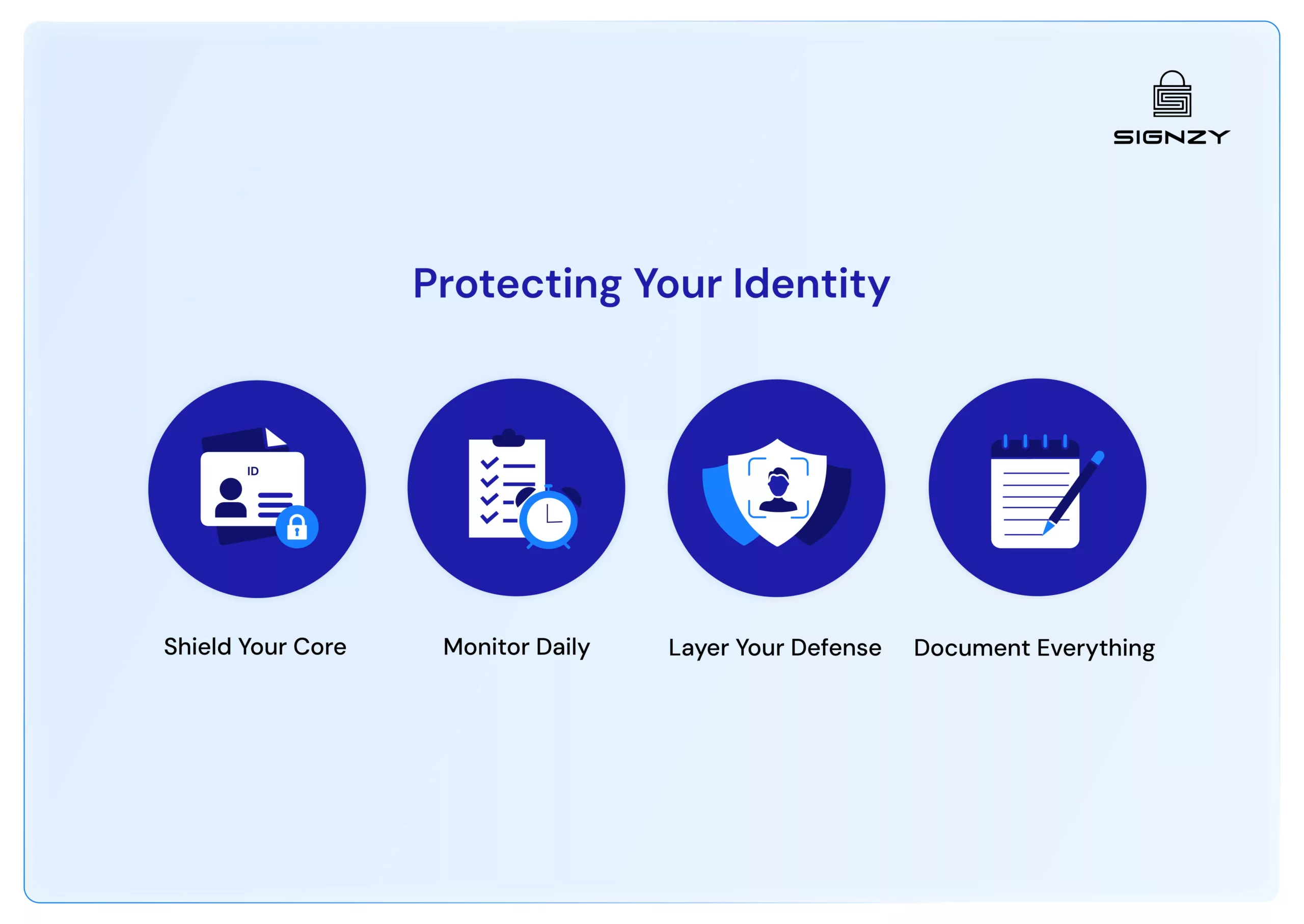
Protecting Your Identity
If you are under attack here’s a general framework you can use:
- Shield Your Core: Secure your essential identifiers first – tax IDs, business licenses, and financial credentials. Use secure storage and require multi-person approval for any changes.
- Monitor Daily: Make 15 minutes each morning count: review account alerts, check for unauthorized changes, and verify any unusual requests. Quick catches prevent big problems.
- Layer Your Defense: Combine human oversight with automated checks. Use identity verification tools for new business relationships, real-time monitoring for transactions, and face verification for remote interactions.
- Document Everything: Keep detailed records of all verifications, suspicious activities, and security measures. Good documentation isn’t just for compliance – it helps spot patterns and improve protection.
While this general framework is straightforward, implementing it can feel overwhelming, especially with limited resources. But yes, there’s a solution.
At Signzy, we get it – you need protection that works without creating extra work. Our suite of identity verification tools can handle the heavy lifting for you: checking faces, monitoring transactions, validating documents, and more. Check our solutions today.
FAQs
How quickly should a business respond to suspected identity theft?
Immediate action is crucial. Report to authorities within 24 hours and activate your incident response plan to minimize damage.
What's the first step if business identity theft is detected?
Contact your bank immediately to freeze accounts and prevent unauthorized access, then file reports with law enforcement and credit bureaus.
Are small businesses really at risk for identity theft?
Yes. Small businesses are often primary targets as they typically have fewer security resources than large corporations.
What makes biometric verification more secure than traditional methods?
Biometric data is unique to each individual and harder to replicate, especially when combined with liveness detection technology.