Knowledge Based Authentication: Process, Role in KYC, and More
- Knowledge-Based Authentication (KBA) is a premium second-factor authentication method that provides a high level of identity verification assurance.
- The IRS has made KBA a requirement for taxpayers to electronically sign their tax returns using Forms 8879 and 8878, underlining its importance in secure digital transactions.
- In situations where alternative identification methods are not available, state notary laws and regulations often mandate the use of KBA for remote online notarization.
Every authentication system guards two gates: security and user experience. While passwords protect the first gate, they often stumble at the second. Biometrics smooths out the experience but adds complexity to the implementation.
Knowledge-based authentication (KBA) bridges this gap effectively. However, its success depends entirely on how you implement it.
If you have the next 6 minutes, we’re covering everything you need to know about Knowledge Based Authentication – it’s basics, implementations, pros, cons and more.
Let’s directly dive in.
What is KBA?
Knowledge-based authentication verifies user identity by requiring answers to personal questions that only the legitimate user should know. When implemented properly, it adds an essential security block to protect sensitive business operations and customer data.
The concept is straightforward. In short, instead of relying solely on passwords, KBA asks users to prove their identity through information specific to them. This could range from their mother’s maiden name to details about their recent transactions.
Before we see how it works, let’s see different types first.
So there are three primary types of KBA, and each serves different security needs:
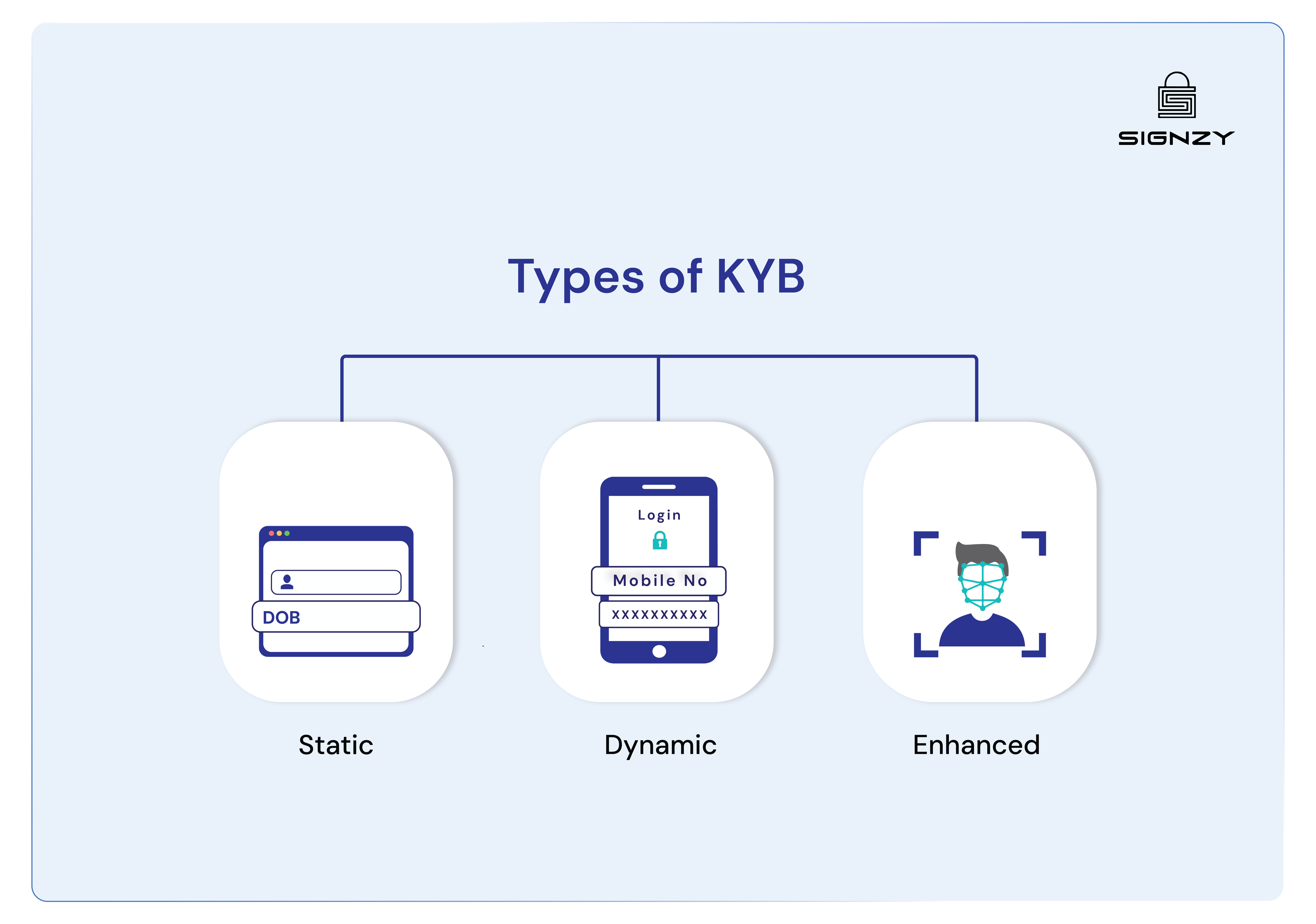
- Static KBA: Users select and answer security questions during account creation – think questions like “What was your first pet’s name?” While this method is familiar to most users, its effectiveness depends heavily on choosing questions that strike the right balance between memorability and security.
- Dynamic KBA: Rather than using preset questions, it generates real-time queries based on information from credit reports, marketing databases, and transaction histories. For example, a user might need to identify a previous address from multiple options. This approach makes it significantly harder for unauthorized users to guess or research the answers.
- Enhanced KBA: It combines both static and dynamic methods, often incorporating additional security measures like biometric verification. The information stays protected behind a secure firewall, making it particularly valuable for high-risk transactions or sensitive data access.
Okay, so that was all about types. Now, it’s time to understand the application.
How Does Knowledge Based Authentication Work?
It works by a mechanism called “Out-of-Wallet Verification”.
Here, the system draws questions from information that wouldn’t typically be found in a stolen wallet or basic identity theft.
In practice, KBA functions through a structured verification process.
- Step 1: The system first validates basic identification details like name and date of birth.
- Step 2: Depending on the security level needed, it presents either static or dynamic questions.
- Step 3: For dynamic questions, the system pulls information from various databases in real-time, ensuring the questions remain relevant and secure.
- Step 4: It verifies the answers and decides whether the authentications are successful or not based on your preset conditions.
Businesses can configure controls at both account and group levels, managing how users interact with the authentication process. This includes setting attempt limits and determining when additional verification might be needed.
But note that KBA works best as part of a broader security strategy. While it provides valuable protection, it might not be effective to meet KYC and other compliance requirements when used standalone.
KBA’s Role in KYC Processes
What makes KBA particularly valuable is its ability to complement other verification methods. For instance, while document verification confirms what a customer has, KBA validates what they know.
In KYC workflows, KBA questions come from reliable data sources that are not typically found in standard documentation.
This “out-of-wallet” information makes verification more secure because the answers aren’t easily available through stolen documents or social media research. Instead, questions might reference past mortgage applications, vehicle registrations, or specific transaction patterns known only to the genuine customer.
KBA also supports KYC’s ongoing due diligence requirements. Rather than just verifying identity during the initial account opening, it helps monitor and validate customer identity throughout the business relationship. This continuous verification becomes especially valuable when customers attempt high-risk transactions or make significant account changes.
How to Setup Knowledge Based Authentication
Just before we start, let’s clear one thing. The process below does not discuss step zero of the process. Basically, understand your specific requirements and user base characteristics before starting to perform Knowledge Based authentication.
Keeping that in mind, here’s how you can perform KBA successfully in 6 steps:
- Set Up Initial Verification Requirements and Parameters
Go to your identity verification dashboard to set matching rules and validation parameters. Basically, configure your system to validate basic user information against trusted databases. You’ll also need to configure API connections to identity verification services and establish data validation rules in your security management console.
- Implement Question Generation Protocols
Create a comprehensive question bank for static KBA or establish secure connections with verified data sources for dynamic question generation. This takes place in your authentication management system, where you’ll set up question pools, configure dynamic data source connections, and establish question selection algorithms. For dynamic KBA, you’ll need additional configuration in your data integration layer.
- Configure Security Controls and Access Management
Head to your system’s security administration panel now to configure access levels, attempt limits, and recovery procedures. Establish controls for both administrator access and user verification attempts.
You’ll also need to set up corresponding rules in your user management system and monitoring dashboard.
- Create Response Validation and Verification Mechanisms
Develop precise systems for answer verification, including allowances for common variations in user responses. This configuration occurs in your authentication validation engine, where you’ll set up matching algorithms and response validation rules. You’ll also configure these settings in your security policy management interface.
- Establish System Integration With Existing Security Infrastructure
Connect KBA processes with other authentication methods and security systems. This integration happens at multiple points – your authentication server, security token service, and identity provider interfaces. You’ll need to configure connection parameters in each system’s integration panel.
- Set Up Monitoring and Maintenance Protocols
Implement comprehensive tracking of verification attempts, success rates, and potential security issues. Set up alerts, reporting parameters, and review schedules. Also, configure logging settings in your audit management system.
Related Resources
Pros and Cons of KBA for Businesses
Like anything, KBA also has trade-offs between protection and convenience. Here’s what’s best and what’s not.
| Pros | Cons |
|---|---|
| Enhanced Security: Adds an extra verification layer through personal knowledge checks | Vulnerability to Social Engineering: Answers might be obtained through research or social media |
| Cost-Effective Implementation: Requires minimal hardware and technical infrastructure | Data Breach Risks: Stored answers could be compromised in security incidents |
| User Familiarity: Most users understand and expect security questions | Information Accuracy Issues: Users might forget answers or provide inconsistent responses |
| Customizable Security Levels: Adjustable for different transaction risks | Limited Effectiveness: May not work well for users with minimal financial history |
| Compliance Support: Helps meet regulatory requirements | NIST Considerations: Not recommended as a sole authentication factor |
| Non-Credit Based Options: Can use various data sources for verification | Privacy Concerns: Dynamic KBA requires accessing personal data |
Getting Started with KBA
As you saw from the pros-cons table, it’s clear that implementation and using KBA with more sophisticated security measures can reduce limitations. For example, pairing KBA with identity verification and biometric checks creates multiple layers of security that complement each other.
Modern identity verification solutions, like Signzy’s APIs, can help streamline this integration. Our APIs handle the complexity of connecting different verification methods, managing data sources, and maintaining security compliance.
By using standardized API connections, businesses can implement robust identity verification without building complex systems from scratch.
FAQ
What is Knowledge-Based Authentication (KBA) in KYC?
How does dynamic KBA improve identity verification?
Why is KBA important in digital onboarding?
What are the risks or limitations of using KBA?

Tanya Narayan
Tanya is a Product Marketing Manager at Signzy and a GrowthX Fellow, with a strong focus on SaaS and fintech. She specializes in go-to-market strategy, customer research, and positioning to help teams bring products to market effectively. She has also cleared the Company Secretary foundation level, reflecting her grounding in corporate and compliance fundamentals.


