What Is Layering In Money Laundering?
- Layering involves moving illegally acquired money through various accounts and geographies to make it difficult to trace its origins.
- According to the UNODC, $800 billion to $2 trillion gets laundered annually. This is around 2-5% of the global GDP.
- Businesses involving banking and financial services are most exposed to the threat of money laundering and layering and need to take active measures to avoid and flag such transactions.
According to the United Nations Office on Drugs and Crime (UNODC) around $800 billion to $1.2 trillion gets laundered annually. This number is around 2-5% of the global GDP. To counter this rising threat, the global anti-money laundering (AML) software market is expected to reach $2.77 billion by 2025. Money laundering is a growing issue for businesses involved in banking and financial services.
Related Solutions
In this blog, we will understand all these three stages of Money Laundering in detail, how they affect your business, and how your business can counter them.
The Process of Money Laundering
Money laundering is an illicit act that involves putting illegally earned money through various transactions and processes to make it look like it was earned from a legitimate source. This could in turn be easily used by the criminals without raising suspicions of the government.
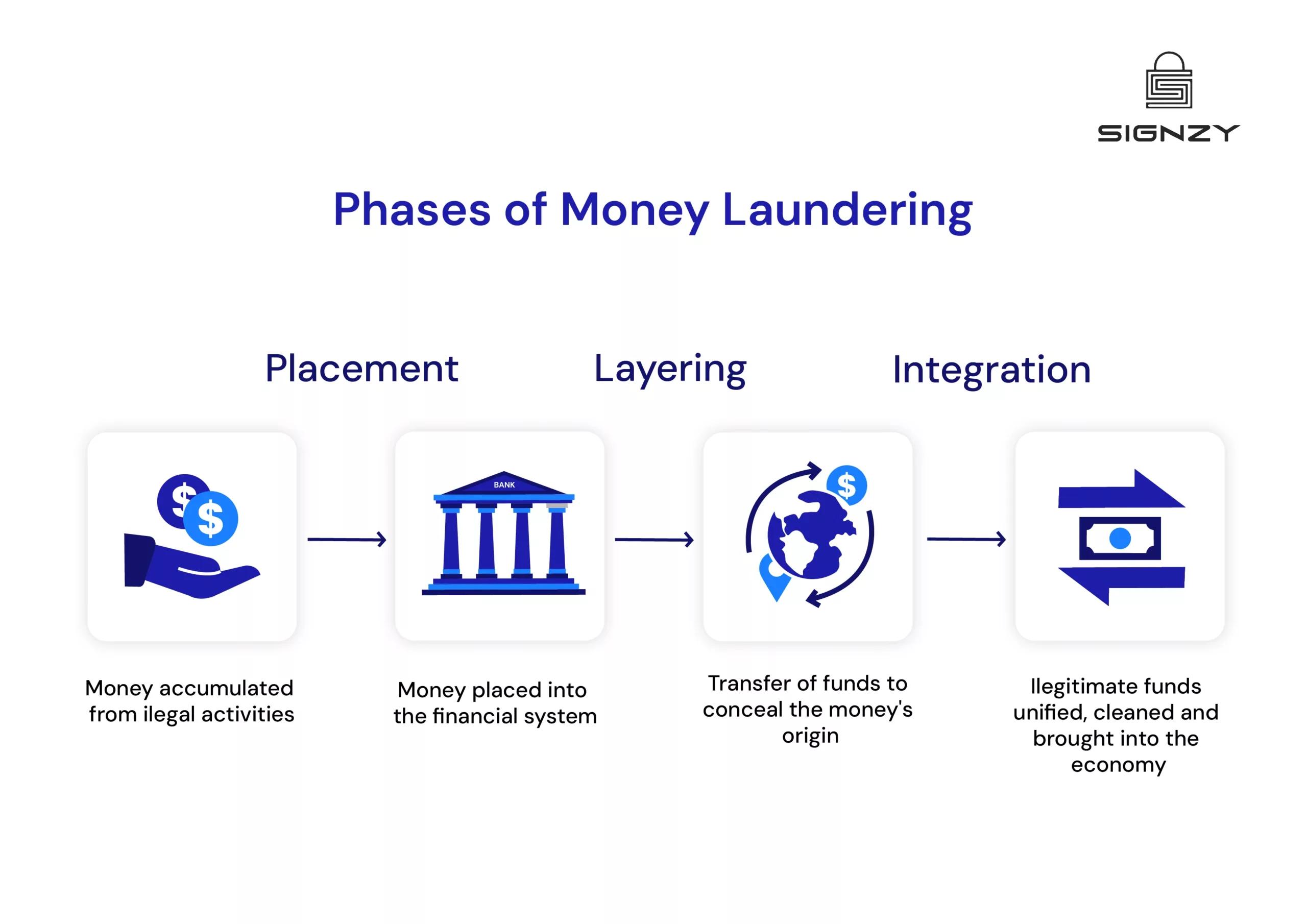
Typically the money laundering process consists of three stages namely placement, layering, and integration. Let’s take a look at each of these steps.
Stage 1: Placement
In the first phase of the money laundering process, the illicit money is entered into the financial system. This is done by depositing large sums into banks, buying assets (like real estate or luxury goods), or exchanging the money into different currencies. To avoid detection, in most cases, a large sum of money is broken down into smaller amounts to prevent triggering any red flags by the government or other officials.
Criminals may also use accomplices, like family or friends, to deposit or transfer the funds into multiple accounts, making it harder for authorities to trace the origin of the money.
Here are some more common methods criminals might use in the placement phase:
- Cash couriers where the money being laundered is physically moved across borders.
- Money mules which involves a third party that receives and transfers the money being laundered, with or without their knowledge.
- Structuring or smurfing where a large amount of money is broken down into smaller chunks. These chunks allow making deposits with banks or financial institutions without raising any alarms.
- Purchase of monetary instruments like money orders, traveler’s checks, or cashier’s checks.
- Buying foreign currencies
- Purchasing high-value assets like real estate, luxury goods, and more where the use of large sums of money might not raise suspicion.
Stage 2: Layering
Layering is the next step after placement. The point of this step is to further mask the origin of illegal funds so that it is as far from the source as possible.
The primary goal of the second stage of money laundering i.e. layering is to obscure or conceal the money’s origin, distancing it further from its criminal source.
Stage 3: Integration
Integration is the final and last stage of the money laundering process in which the illegitimate funds are then unified back into the economy. In this stage, the money has been “cleaned” and is made available for use.
This was a brief of the three steps in money laundering. Banks and other money service businesses have the highest exposure to the layering phase of money laundering. Businesses may catch flak for housing accounts that are linked to the many involved in layering illegal money. So to better counter layering and money laundering at large, let’s take a closer look at the second stage which is the layering phase of money laundering.
Layering in Money Laundering
Here are some of the most common methods used during layering:
1. Transferring Funds Between Multiple Accounts (Domestic & International)
Criminals often use a tactic known as “layering through accounts” to create a labyrinth of transactions that becomes difficult to trace. They might transfer illicit funds from one account to another, both within the same financial institution or across multiple organizations, including offshore accounts in jurisdictions with weaker anti-money laundering (AML) controls.
Key Tactics:
- Internal Transfers: Funds may be moved between various accounts owned by the same person or criminal network, making the transactions appear legitimate, but in reality, it’s just a paper trail designed to confuse authorities.
- International Transfers: Here, money is moved to and from banks in different countries, especially jurisdictions with low AML regulations (known as “tax havens” or “offshore banking centers”). Some popular jurisdictions for this method are the Cayman Islands, Switzerland, and Panama. By doing this, criminals can hide the trail of the money and make it harder for authorities to track.
Transferring funds between multiple accounts creates a complex paper trail, which can overwhelm investigators and make it difficult to pin down the origin of the money. Additionally, the use of international transactions and offshore accounts can exploit gaps in international financial monitoring.
2. Creating Shell Companies and Front Businesses
Criminals often use shell companies or front businesses as a way to launder money by disguising it as legitimate business revenue. Shell companies are entities that have no real business operations or assets but are legally registered to operate in certain jurisdictions. These companies can be used to create false paper trails and hide illicit funds.
Key Tactics
- Fake Business Transactions: Illicit money is funneled through these shell companies as “business revenue,” with criminal organizations either inflating the company’s earnings or fabricating false invoices for services or products that were never actually provided.
- Mixing Dirty Money with Legitimate Business Funds: Criminals might use legitimate companies to commingle illegal funds with legitimate business revenues. For example, money earned from criminal activities might be deposited into a legitimate company’s bank account and then processed as legitimate income. Businesses like restaurants or casinos(which typically handle a lot of cash) are often used for this.
- Offshore Shell Companies: Criminals may also set up shell companies in tax havens or jurisdictions with weak corporate transparency laws (like Panama, the British Virgin Islands, or Luxembourg). These companies can act as a cover for illicit transactions, such as routing illegal funds through various accounts or businesses.
Shell companies provide a convenient way to hide ownership of illicit money and create the illusion of legitimate business operations. They allow criminals to manipulate financial records and hide the true ownership of assets, complicating efforts to trace the source of funds.
3. Buying and Selling High-Value Assets like Real Estate and Luxury Goods
Criminals often turn to physical assets such as real estate, luxury cars, artwork, or jewelry to layer their illicit funds. By buying and selling assets, they can effectively “wash” the money, making it appear as if it comes from legitimate transactions.
Key Tactics:
- Over or Under-Valuing Assets: One common strategy is to over or under-value assets like real estate or jewelry when buying or selling them. For example, a person trying to launder money may buy a property at an inflated price and sell it for a lower price, the “loss” on the transaction allows them to move illegal funds without raising suspicion.
- Flipping Assets: bad actors may buy an asset and quickly sell it to another party in an attempt to distance the funds from their criminal origin. The goal is to create transactions resembling seemingly legitimate sales and purchases.
- Layering Through Luxury Goods: Luxury goods such as expensive cars, watches, and artwork can be bought using illicit money and then resold, with the funds now appearing “clean.” These goods are often sold through intermediaries, like auction houses or high-end dealers, which further helps obscure the true nature of the transactions.
Physical assets like real estate and luxury goods have intrinsic value and are relatively harder to trace compared to cash. The buying and selling of these items provide a way to launder money in a manner that appears normal in the marketplace.
4. Using Currency Conversions and Cryptocurrencies
Criminals may convert illicit cash into foreign currencies through currency exchange services or bank transfers. They may engage in multiple currency exchanges, or use cryptocurrencies to move funds across borders or through financial systems.
Key Tactics:
- Multiple Currency Conversions: Funds may be exchanged from one currency to another (for example, U.S. dollars to Euros, and then to Japanese yen) to create a confusing chain of transactions. This process can be done multiple times in different financial centers, further obscuring the origin of the money.
- Using Cryptocurrencies: Some criminals turn to cryptocurrency exchanges to layer money. Cryptocurrencies like Bitcoin, Ethereum, and others allow for relatively anonymous transfers and can be exchanged globally. Criminals often use peer-to-peer exchanges or private wallets, making it difficult for regulators to trace the flow of funds. Transactions in crypto can be conducted without the oversight of traditional financial institutions, which further complicates detection.
- International Wire Transfers: Money may be sent across borders via wire transfers, often using multiple intermediaries or “layering” banks to further distance the funds from their illicit origin. These transfers can be structured to bypass reporting thresholds or to make it difficult for authorities to follow the money trail.
Currency exchanges and international transfers make it easier to mask the movement of illicit funds, especially when using digital currencies or peer-to-peer methods. The use of various currencies or cryptocurrencies adds an additional layer of complexity, making it harder to follow the money through traditional financial systems.
5. Misusing Trusts, Offshore Accounts, and Financial Instruments
Criminals may establish trusts or use offshore accounts to hold or conceal illicit funds. These trusts are often set up in jurisdictions with strong privacy laws, making it difficult for authorities to determine the true ownership of the funds.
Key Tactics:
- Offshore Accounts: Funds may be transferred into offshore accounts or tax havens, where financial regulations are lax and bank secrecy is stronger. These accounts can be opened in the name of a nominee or a trusted associate, who acts as a “front” for the criminal.
- Financial Instruments: In some cases, criminals use complex financial instruments, such as life insurance policies, derivatives, or bonds, to layer illicit funds. These instruments can be used to move money or disguise the origin of funds by creating complex financial structures.
- Trusts and Foundations: Criminals might also set up trusts or private foundations to hold assets on their behalf. These structures often hide the identity of the true beneficiary, which makes tracing illicit funds much more challenging for law enforcement.
Offshore accounts, trusts, and financial instruments provide an added layer of secrecy, making it more difficult to trace the true ownership of the funds. These methods also allow criminals to use their illicit money while keeping it out of the reach of authorities.
How Signzy can help Your Business Counter Layering and Money Laundering
Countering money laundering is becoming a growing need for businesses. With the increasing number of ways bad actors can launder money, the best course of action is to introduce professional third-party services into your business’s operations. These third-party apps can help streamline the many ways your business can counter money laundering and remove the risk of human errors.
Signzy’s Bank Account Verification API can help businesses check and authenticate the identities of beneficiaries of a bank account to better gauge the nature of transactions. This can help businesses flag transactions with accounts that have illegitimate or suspicious origins.
On top of this, our Business Verification API provides a holistic check of organizations that your business may transact with. This added layer of identity verification can help avoid or flag any transactions with businesses that may have suspicious origins and/or operations.
Conclusion
Knowing the problem is the first step to solving it. Armed with the information in this blog, it should now be easier to detect, flag, and report any suspicious activities with your business. Of course, the use of professional third-party services like Signzy’s API Marketplace can help make this process more efficient. However, businesses need to be updated with the changing environment of security as well as crimes to better counter them.
FAQ
What is an example of layering?
What are the three layers of money laundering?
What is Customer Due Diligence in a bank?

Agrima Dwivedi
Agrima is an Associate Product Marketer at Signzy, currently working in the B2B fintech space. She brings over two years of experience in copywriting and content writing, which laid the foundation for product marketing. Today, she leverages both creative and strategic skills to drive go-to-market efforts and build user-focused marketing strategies.