What is an NFC tag? Difference Between NFC Tag and Chip
November 25, 2024
7 minutes read
 Key Highlights
Key Highlights- Over 2 billion NFC-enabled devices exist globally, with 20% of the world’s population currently having access to NFC technology.
- NFC operates only within a tiny 4-inch (10-centimeter) range, making it one of the most precise secure communication technologies
- Each NFC tag generates unique cryptographic signatures, making genuine tags virtually impossible to clone
If passwords and authentication codes had a family reunion, NFC tags would be that cool cousin who shows up and makes everyone else look outdated. You know, the one who actually gets things done without making a fuss about it.
Because that’s exactly what these tiny tags are – effortlessly practical. Need to onboard a user easily? Done. Want to verify high-value transactions without making customers jump through hoops? Sorted.
And unlike most business technology that promises the moon but delivers a headache, these tags actually do what they’re supposed to.
They just work. Tap, verify, done – as natural as checking your phone.
In this guide, we’ll show you can use these tags to add an invisible layer of security to sensitive operations, without adding friction to customer experience. And it starts right below.

What is an NFC Tag?
In its simplest form, an NFC tag is a small electronic component that communicates wirelessly with smartphones and other NFC-enabled devices.
Think of it as a miniature radio station that only broadcasts when another device comes very close (within a specific range of 4 inches/10 centimeters).
What makes these tags particularly practical is their self-sufficient nature.
Unlike other wireless technologies that need constant power, NFC tags stay dormant until activated by another device, making them both cost-effective and environmentally conscious.
Components of NFC Tags
The magic of NFC happens through three essential components:
- The Chip: Each chip further contains a dedicated memory unit, communication processor and security elements. The memory capacity ranges from a modest 48 bytes in basic tags (enough for a website link) to 32 kilobytes in advanced versions (capable of storing detailed security credentials).
- The Antenna: The antenna might look like a simple coil of wire, but it’s precisely engineered to create and maintain the magnetic field necessary for communication and convert radio waves into usable electric current. Moreover, it’s also engineered to enable data transmission through electromagnetic coupling.
- The Substrate: This protective layer shields the internal components while maintaining the tag’s functionality.
Now comes the real benefit:
Organizations considering NFC tags don’t need to stress about whether they’ll be able to make their users adopt it or not. Over 2 billion devices now come equipped with NFC capabilities, with 20% of the global population having access to this technology in the form of devices like Mobile and PCs.
Are NFC Tags and NFC Chips Different?
Yes, 100%. While often confused, NFC tags and chips serve different roles in the ecosystem. NFC chips are active components found in smartphones and payment terminals, while tags are passive elements that come to life only when activated by these chips.
Here’s how they stack up against each other:
| Feature | NFC Tags | NFC Chips |
| Power Source | Passive (powered by a reader) | Active (needs constant power) |
| Memory | 48 bytes – 32 KB | Several MB |
| Cost (average) | $0.10 – $3 per unit | $5 – $30 per unit |
| Data Transfer | One-way (usually) | Two-way |
| Security Features | Basic encryption | Advanced encryption, secure element |
| Size | Very small (millimeters) | Larger (centimeters) |
| Integration | Simple attachment | Complex circuit integration |
How NFC Tags Work?
The interaction between NFC devices follows a precise choreography of wireless communication. When a smartphone comes near an NFC tag, it generates a magnetic field, which awakens the dormant tag.
This field creates something called magnetic induction – essentially wireless power transfer – allowing the tag to transmit its stored data back to the phone.
The data exchange happens through encrypted channels protected by multiple security layers:
- Basic Access Control (BAC): Acts as a digital bouncer, checking credentials before allowing access
- Password Authenticated Connection Establishment (PACE): Creates a secure tunnel for data transmission.
- Active Authentication: Verifies the authenticity of both devices involved
What makes this process particularly secure is its one-to-one nature. NFC tags can only communicate with a single device at a time, significantly reducing the risk of unauthorized data interception.
Why Does NFC Stand Out? NFC vs. Other Technologies
| Feature | NFC | RFID | Bluetooth | QR Codes |
| Range | 4 inches | Up to 300 feet | 30-300 feet | Visual line of sight |
| Power Need | None (passive) | Varies | Constant | None |
| Security | High | Medium | Medium-High | Low |
| Cost | Low-Medium | Low | Medium | Very Low |
| Speed (average) | 424 Kbps | 424 Kbps | 2.1 Mbps | Instant |
| Device Support | Most modern phones | Needs reader | Universal | Camera needed |
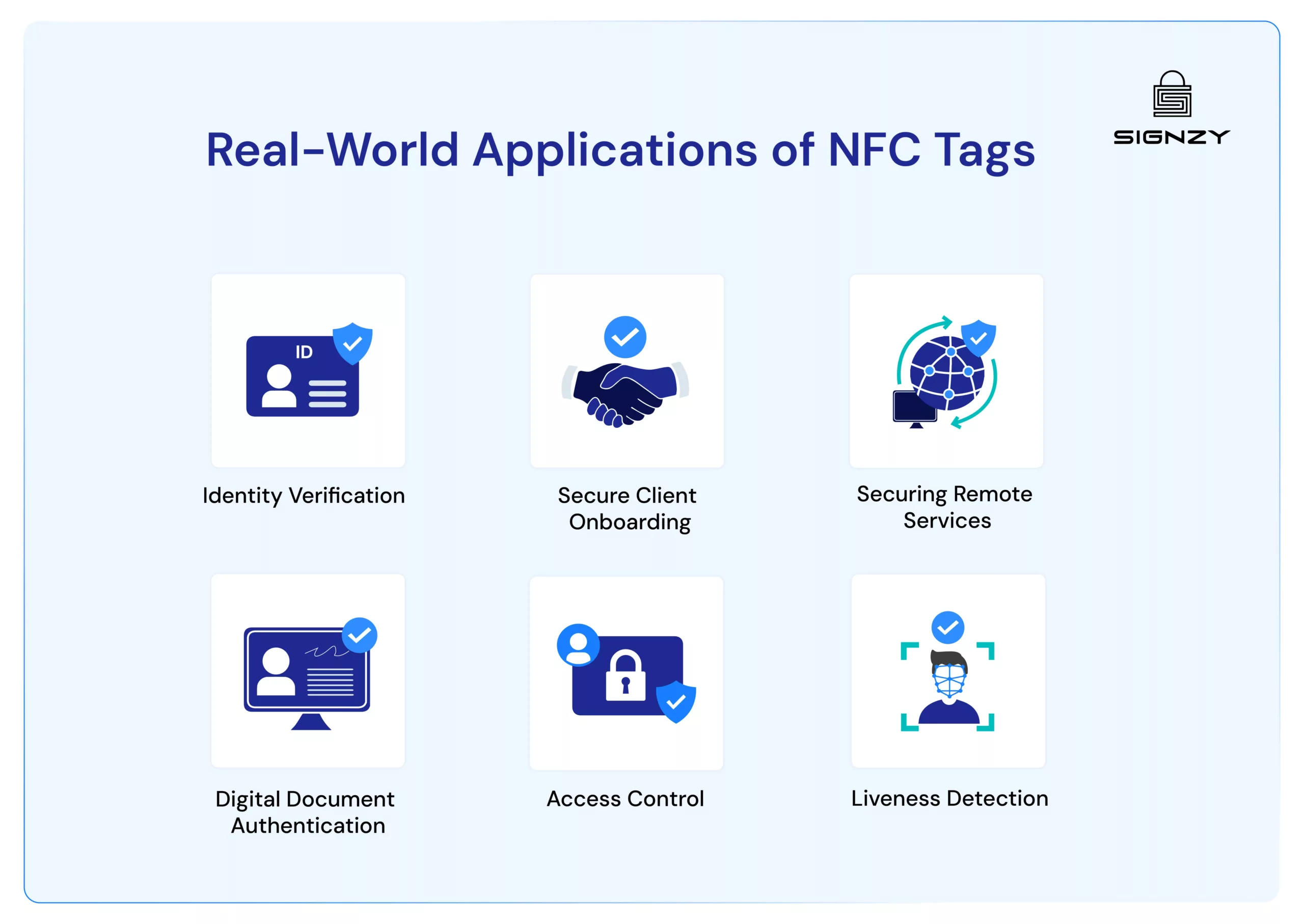
Real-World Applications of NFC Tags
Basically, it solves two seemingly opposing challenges:
maintaining airtight security while creating smooth, friction-free experiences.
While NFC tags pop up everywhere – from retail stores to transit systems to smart homes – we are focusing on what matters most for financial institutions and businesses handling sensitive customer data.
-
Identity Verification
Gone are the headaches of manual KYC checks and endless document verification loops. Businesses can now verify customer identities in real time by simply having them tap their ID against a phone.
The encrypted biometric data stored in modern IDs matches against live selfies, creating a verification process that’s both tough to fool and remarkably simple. Banks and financial institutions particularly love this because it ticks all their compliance boxes while keeping the process quick and customer-friendly.
-
Secure Client Onboarding
Onboarding a new user used to mean paperwork – lots of it. Now, NFC-enabled document verification makes this process almost entirely digital. When a customer presents their passport or ID, the NFC reader extracts cryptographically signed data that’s virtually impossible to forge.
With this, banks, financial institutions, fintechs, and similar businesses can instantly validate government IDs, cross-reference biometric data, and create secure customer profiles in minutes instead of days.
This means faster service for customers and better fraud prevention for businesses – a genuine win-win situation.
-
Securing Remote Services
The shift toward digital banking has made remote verification essential. NFC technology enables financial institutions and crypto platforms to verify customers’ identities remotely with the same level of certainty as in-person checks.
Whether it’s opening new accounts, authorizing large transactions, or updating customer information, NFC-based verification provides a secure, contactless way to confirm customer identities without requiring branch visits.
-
Digital Document Authentication
The challenge with digital documents has always been proving they’re real. NFC tags embedded in official documents can serve as digital seals of authenticity. When scanned, these tags reveal encrypted certificates that confirm the document’s origin and detect any tampering attempts.
For financial institutions handling sensitive documents, this technology has become invaluable in preventing fraud while speeding up document processing.
-
Access Control
Modern office buildings and secure facilities now use NFC-enabled employee badges that do much more than just open doors.
These smart badges track access patterns, manage different security clearance levels, and even integrate with time and attendance systems. The switch from traditional access cards to NFC has cut down security breaches by creating unique, encrypted identifiers for each access attempt.
-
Liveness Detection
NFC tags work hand-in-hand with liveness detection to create a powerful anti-spoofing system.
When a customer presents their ID, the NFC chip provides encrypted biometric data that’s matched against real-time liveness checks. This dual-layer verification confirms not only that the ID is authentic but also that a real person is present during the verification.
Take Action
At Signzy, we understand the challenges of balancing secure verification with smooth customer experiences. While NFC technology adds a powerful security layer, it’s the seamless integration that makes all the difference.
Our identity verification suite – particularly our Face Match API and Liveness Check API – works hand-in-hand with NFC authentication to create verification flows that feel effortless to customers while giving you bank-grade security.
Ready to see how we can help strengthen your verification process? Let’s chat – book a demo today.
FAQs
How secure are NFC transactions?
Modern NFC implements multiple encryption layers and secure element protection, making unauthorized access extremely difficult. Each transaction creates unique encryption keys.
What's the difference between passive and active NFC devices?
Active devices (like phones) provide their own power and can both read and write data. Passive devices (tags) activate only when powered by an active device’s magnetic field.
Do NFC tags work through cases or wallets?
While NFC can work through thin materials, metal cases or thick wallets might interfere with the magnetic field, reducing effectiveness. The optimal distance remains 4 inches or less with minimal interference.
Can a single NFC tag store different types of data?
Yes, NFC tags can store various data types including text, URLs, and encrypted credentials. However, storage capacity varies by tag type, ranging from 48 bytes to 32 kilobytes.