What Is Email Verification? How It Powers KYC, KYB & Compliance Explained
- Fake or temporary emails are often used for fraudulent activities. Without proper verification, you could unknowingly allow malicious users access to your platform, leading to financial loss or data breaches.
- Outdated or invalid emails are a major reason for low engagement rates. If you don’t verify emails regularly, your email list can slowly become ineffective, impacting customer communication and retention.
- Businesses are required to ensure their data collection methods are accurate, including email addresses. Failing to do so could risk non-compliance with regulations like GDPR or CCPA, potentially leading to fines.
Businesses don’t remember all their users by name or face right? You most probably have their email address and contact details at hand.
So, before you can verify someone’s identity through advanced KYC protocols, before running background checks or verifying documents, there’s a critical first domino that must fall: confirming that the provided contact email is real and actually belongs to the right person.
Every unverified email in your system creates a cascading effect.
- Marketing teams craft personalized campaigns that never reach real eyes.
- Sales teams chase leads that don’t exist.
- Support teams maintain resources for phantom users.
And most critically, your KYC and KYB processes build on a foundation that might be entirely false.
The good news is: the email verification process is not that tough and you can stop this chain reaction. We’ve packed everything you need to know in this comprehensive guide – takes 6 minutes.
Let’s dive in.
💡 Related Blog:
What is Email Verification?
Email verification is the process of confirming whether an email address exists and belongs to the intended person. In its simplest form, it determines whether an email address can receive messages. At a more sophisticated level, it evaluates the reputation and authenticity of email addresses to protect businesses from fraud and maintain communication quality.
The most critical times to verify email addresses are:
- At account registration or signup
- Before sending email campaigns
- During suspicious activity detection
- For regular database maintenance
- Before major business transactions (better safe than sorry)
- When updating customer records
Email verification can be thought of as the foundation stone of digital identity – if an email isn’t real, nothing else in the verification chain can be trusted.
How Does Email Verification Work?
Behind every email verification lies a sophisticated series of checks, each building upon the last to ensure validity and functionality.
Here’s a topline overview. Email verification works by:
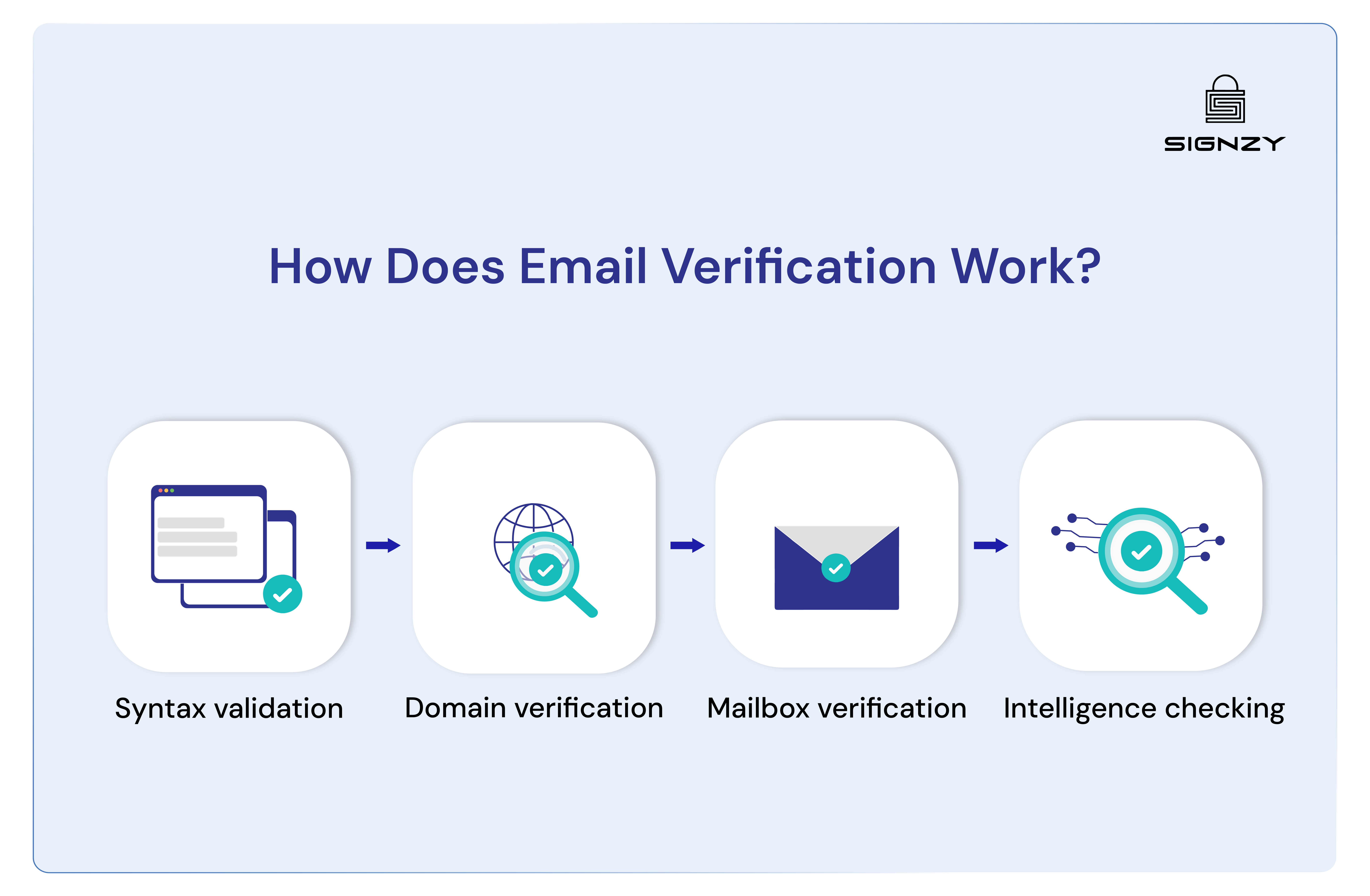
Syntax Validation ▶️ Domain Verification ▶️ Mailbox Verification ▶️ Intelligence Checking
Here’s a more detailed answer explaining all touchpoints:
- Syntax validation: The basic structure check. An email needs correct formatting and standard syntax. The system examines everything from the @ symbol placement to the proper construction of the domain name.
- Domain verification: This stage asks a critical question: does this email’s home actually exist? And by checking DNS records, validating MX records, and confirming active status, this step ensures the email has a real destination.
- Mailbox verification: This touchpoint takes it further, confirming whether the specific email address exists on that mail server. Through SMTP protocol checks, it determines if messages can actually reach their intended recipient. Nowadays, businesses prefer opt-ins, which send subscription confirmation emails to recipients to double-verify addresses.
- Intelligence checking: This serves as the final guardian, analyzing patterns and reputation. It spots red flags like disposable email services, role-based addresses, and known problematic patterns that could signal trouble ahead.
There are various types of email verification methods, and touchpoints can vary accordingly. However, you can understand the basic flow from the above answer. Now let’s see those various types of email verification methods.
Types of Email Verification Methods
The path to reliable email verification is not one-size-fits-all.
There are many methods. Each method serves distinct business needs, and sometimes, combining approaches creates the strongest shield against invalid data.
We are not complicating things for you. Here are the primary ones that are used extensively across the world to meet high compliance and security standards.
Real-time API Verification
It goes like: a customer enters their email address, and within milliseconds – before their finger leaves the mouse button – the system knows if it’s valid. API is connected to the databases (Gmail or Outlook for example) and then they handle this instantaneous check by:
- Validating format and syntax
- Confirming domain existence
- Checking mailbox accessibility
- Analyzing email reputation
As a result, problems stop at the door, keeping databases clean from day one. More on this in a minute.
Batch Verification
When dealing with existing email lists, batch verification steps in as the practical solution. It’s particularly valuable during database cleanups or before major email campaigns. The system processes thousands of addresses simultaneously, providing detailed reports about each email’s status.
Two-step Verification
Sometimes called double opt-in, this method adds a human element to technical verification. After initial automated checks, the system sends a confirmation email requiring user action.
While adding an extra step, it virtually eliminates the risk of false positives. This method has become a must-have lately as businesses often experience low bounce and spam rates compared to traditional methods.
Regardless of the method you like, make sure you at least pick one since strong email verification has extended from merely being a good practice. It’s often legally required as it protects both businesses and their customers from significant risks.
Email Verification and Regulatory Compliance
Email verification proves invaluable across various compliance frameworks.
Role in KYC
Before diving into documents or background checks, organizations need one reliable starting point – a verified email creates exactly that. This initial verification enables secure document sharing, establishes clear communication channels, and contributes to risk assessment.
Most importantly, it builds the foundation that makes all subsequent KYC steps more reliable and meaningful.
Role in KYB
Business verification requires extra layers of certainty, starting right at the email domain level. A properly verified corporate email is necessary: it speaks to domain ownership, connects to authorized personnel, and establishes a business’s digital legitimacy.
This verification creates a secure channel for sharing sensitive business documentation. It’s precise, purposeful, and essential.
Related Solutions
Role in AML Compliance
Email verification stands as a sentinel in anti-money laundering efforts. It spots concerning patterns early, making transaction monitoring sharper and more effective.
When investigating suspicious activities, verified emails help connect related accounts and maintain clear audit trails. This creates a stronger monitoring system where suspicious patterns become harder to hide and easier to track.
Role in Data Protection
Protecting sensitive data starts with absolute certainty about who receives it. Email verification ensures this certainty while maintaining proper consent records and enabling precise access management.
Every communication flows through verified channels, creating an environment where data moves securely and every interaction leaves a clear trail. It transforms data protection from a concern into a natural outcome of proper verification.
Automating Email Verification
A well-implemented verification system operates invisibly while providing robust protection.
The key lies in implementing verification thoughtfully – choosing the right automation methods and integrating them seamlessly into existing workflows. When done right, email verification strengthens compliance, enhances security, and builds customer trust – all while operating smoothly in the background.
For organizations handling high volumes, modern verification systems, especially APIs, scale automatically. They maintain consistent performance, whether processing individual sign-ups or bulk database updates. Advanced risk scoring adapts to emerging threats, while detailed reporting provides clear audit trails.
Signzy’s Email Verification API brings these capabilities together in one integration point. Through simple API calls, organizations receive comprehensive verification results, enabling confident decision-making while maintaining strong security standards.
FAQ
How long does email verification take?
What happens when an email fails verification?
Can valid emails fail verification?
Is email verification enough for security?

Saurin Parikh
Saurin is a Sales & Growth Leader at Signzy with deep expertise in digital onboarding, KYC/KYB, crypto compliance, and RegTech. With over a decade of professional experience across sales, strategy, and operations, he’s known for driving global expansions, building strategic partnerships, and leading cross-functional teams to scale secure, AI-powered fintech infrastructure.