Supreme Court Judgement & Re-birth of Privacy
In a recent judgement, a nine-judge Supreme Court Bench unanimously ruled that individual privacy is a fundamental right. The court noted that the “Right to Privacy is an integral part of Right to Life and Personal Liberty guaranteed in Article 21 of the Constitution.” The right to privacy verdict, although primarily passed on a petition filed about the Aadhar Card scheme, will impact every company that collects and handles user data.
In its 547-page judgment, the Supreme Court touched upon the different aspects of informational privacy — and explained how collecting data could threaten an individual’s privacy.
This Supreme Court ruling is a check: For both the government (against which the case was mainly fought) as well as the non-state actors or private companies because it doesn’t just oppose any privacy invasive practices employed by the government but also applies to private companies that collect user data.
In this article we will give a short description of court’s view on what is private and their concerns in a digital world. Then we will look at the new rulings impact on the financial sector with a 7-point framework. We will be looking at areas like cross-selling, credit history, SMS scraping, Aadhar KYC, Payments, Banking Agents, Social behavioral data among others. Now lets start with the basics.
Defining what is “personal and confidential”
The information must be “personal and confidential” to be protected by right to privacy. One of the points raised by the opposing counsel during the trial was that privacy was vague and ill-defined. The judges patiently tried defining what is “private” data, to carve out the scope of law.
For example, the Court pointed out that data about electricity consumption pattern of a person is NOT personal or confidential, and couldn’t be protected as “private information”. That said, the Court also cited a UK judgement that stated the storing of the biometric data indefinitely of individuals no longer suspect of criminal activities would be an invasion of privacy. Clearly, a person’s biometric data is both “personal and confidential”.
The Supreme Court used an infographic (from Bert-Jaap Koops et al., “A Typology of Privacy”) in its judgement to depict the nature of data and its classification. This is extremely rare and hence also shows how judges understood the importance of the judgement and that it would be read by people who might need simpler language and symbols to understand the implications:
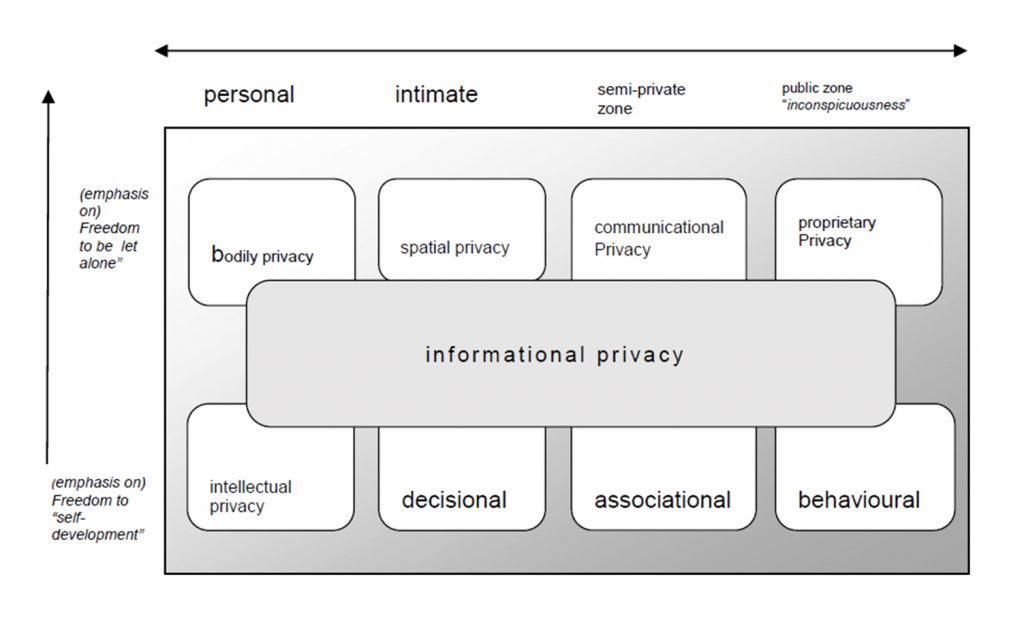
Privacy in the Digital World
While the court had a broader mandate and covered privacy from all aspects,they did cover digital privacy in detail. At some level they felt the real challenge to privacy is coming from this rapid transformation of processes from offline to digital. They also gave an intriguing example of a travel agent, which illustrates this point well:
“The old-fashioned travel agent has been rendered redundant by web portals which provide everything from restaurants to rest houses, airline tickets to art galleries, museum tickets to music shows. These are but a few of the reasons people access the internet each day of their lives. Yet every transaction of an individual user and every site that she visits, leaves electronic tracks generally without her knowledge. These electronic tracks contain powerful means of information which provide knowledge of the sort of person that the user is and her interests. Individually, these information silos may seem inconsequential. In aggregation, they disclose the nature of the personality: food habits, language, health, hobbies, sexual preferences, friendships, ways of dress and political affiliation. In aggregation, information provides a picture of the being: of things which matter and those that don’t, of things to be disclosed and those best hidden.”
Expressing privacy concerns about how tracking happens in the digital world, the Court hinted at the possibility of scrutinizing activities carried on by companies like reading/analyzing/tracking emails, messages, other social behaviour.
Further the court stressed upon properties of the digital world that make it difficult to detect privacy invasion and hence heighten privacy concerns:
- Non-rivalrous — simultaneous use by multiple users
- Invisible — invasions of data privacy are difficult to detect — and it travels at speed of light making it further difficult to trace any breach of privacy. Data can be accessed, stored and transmitted without notice
- Recombinant — data collected can be used, analysed and combined to create more data output which is unseen earlier
Expanding on these principles the order stated that owing to the nature of digital data, it becomes possible to combine data from social profiles and IoT devices to create information about the individual which did not exist. Secondly, while collecting the behaviour of one person it could also be possible to gather information about other individuals around him. The Court noted that these concerns are from both State and Private entities as both use Big Data to analyse data about individuals which is a concern to privacy.
Easily one of the most tech-savvy orders ever, this Supreme Court judgement took into account various technical intricacies of the digital world and cited specific instances:
- Cookies used for tagging IP
- Browsing information to create profiles using algorithms
- Automated content analysis of emails for targeted marketing
- Online purchases like books, airlines, book taxi etc. and their history for user behaviour and doing income analysis
- Metadata and IoT — used to collect information about a person’s behaviour
It is refreshing to see such technical detail quoted in the judgement.
The court also gave details on what can be the future of digital privacy and principles of the new law. We have tried to summarize it below in a simple framework. But for any legal geeks out there we have also created another article which details out laws examined by the court and their approach in reaching to this conclusion.
A 7-point framework to guide companies’ data policies (based on the privacy case judgement)
We’ve analyzed the judgement in extensive detail and have come up with a simple 7-point framework that shows the key points that organizations need to think about when framing their data policies :
Personal vs Private: Every data that is personal is not necessarily private. A user’s name, for example. Because a person’s name is used in public communication, name can be considered to be non-private personal information. Also any information that is anonymized is neither personal or private and exempt from purview of the law.
Explicit Consent in plain words: User’s consent has to be taken explicitly and cannot be hidden inside lengthy terms of service or agreements.
Consent alone is insufficient: Court has also opined that in certain situations, even a consent based mechanism may not be able to protect the customer and hence encroachment of privacy shouldn’t be a preferred option.
Necessity: This is a simple principle which asks the question if collecting it is really necessary to invade privacy to achieve the outcome.
Proportionate benefit or risk: Whenever it is necessary it should be weighed against proportionate benefits and risks. Privacy should not be encroached unless there is some proportionate good possible or some bad that is preventable.
Right to Forget: Eventually the user should have the right to revoke access to his/her data
Access and Correction: The ownership of data is with the individual whose private data is collected. Therefore he has a right to access and correct the data or delete as given above.
Note: We hope this will help businesses make sound and compliant judgement around their data, but do take professional help to make sure you are fully compliant.
Few instances of impact in the financial world
The right to privacy might initiate changes in current processes and hence some of the current and emerging areas may need a relook:
Credit History under Credit Information Act
- Collection of credit data: Collection of credit data by the creditor is completely ok as it is consent-driven private data between the two parties.
- Exchange of credit data: Banks report credit data to licensed agencies. These agencies then exchange this data with other banks as requested by the bank. This might require clear exceptions made in the privacy act or a re-look into how credit reports are requested, what kind of information can be shared and what is to be hidden.
- Access and control over credit history: Currently consumers cannot easily request credit history to be forgotten or edited. Going further there would need to be an option to have greater control and access of one’s own credit history.
Pulling data of a customer from KRA by Mutual Fund and AMCs
- Collection of data: Currently the agency that collects the data and the one that stores the data are different. Clear consent and declarations hence maybe needed.
- Current practice of data pull from PAN, without an appropriate consent layer may also need a relook.
Account Details
- Login based scraping: Account username and password definitely fall into the domain of private data. And the reason in many cases is convenience, as it might be more difficult for the user to submit a copy of bank statement himself. Thus this encroachment may not meet the principle of necessity or proportionate benefit.
- Account Aggregator: The new RBI guidelines provide for a consent layer and a lot of regulation around security of such data. The data does not remain with the aggregator post-completion of the purpose and therefore the guidelines seemed to have given protection to privacy and may not be greatly affected by the judgment.
Mobile data collection during application download
Following are few of affected the categories and let’s go through them one by one:
- Malware or Security risk: The data collected to assess malware risk may not fall within privacy parameter. Specially if it can be anonymized enough to be unlinked to the individual himself. But current assessment tools and processes might need to ensure they follow this principle.
- SMS reading: This is being seen as a new innovative way to provide credit assessment. But within the new privacy regime, this maybe really tricky. Let us explain: SMS reading is a clear invasion into privacy and hence would require explicit consent. But where it gets really tricky is that SMS is usually a private conversation between two parties and hence you would need consent of both the parties to read SMS. It will be interesting to see how the innovation can be enabled without being unlawful.
- Reading personal contacts to use later for collection: Like SMS reading this may also need consent of two parties and hence should be seen in the same light. (Signzy would be coming up with another article on multi-party conversations including email, sms, call etc. We will examine in detail the implications under a privacy law.)
Aadhar based KYC regime
- There are two KYC possibilities in Aadhar A) Demo Auth B) eKYC — biometric or OTP. As the Aadhar regime has a robust consent architecture in place it should hold good even in the present regime. The only concern raised by the court was on biometrics being private. Hence the nature of benefit should be proportionate as consent alone, as noted by the court may not be enough protection. Hence biometric based KYC for account opening, new SIM or other risky scenario might be acceptable. Biometric based KYC for non-risky scenarios such as event registration might need a relook.
- The other more grave change maybe the need for an alternate option. While the financial regulators in line with government view had been pushing a biometric KYC, the current law would require the financial system to provide alternatives. This is especially true for cases where there maybe no real risk or proportionate benefit of forcing biometric KYC.
Users financial transaction history
- Cross-sell: Financial data mining for targeting for another product might definitely fall under invasion of privacy. The judges have clearly defined “financial information” as private. And such targeting in no ways provides “proportionate” benefit. Hence banks will need to take explicit consent in the original account opening form, even then it’s best that such analysis and targeting is totally automated. Closer on the lines of Google’s approach where a Google employee at no point has access to your records even though you are targeted based on your personal data. This will make sure that there is no leakage or profiling and hence the principles are being adhered to. But there would need to be clear regulation to define such actions by the bank.
- AML/CFT risk assessment: This is one use case where the risk may justify privacy invasion. But we need to weigh it against the principle of necessity. Again as it stands out it might not be necessary to invade privacy. The court has enunciated how “anonymity” does provide privacy, and hence analysis of data that has been “anonymized” will not be a breach of privacy. Only when suspect transactions are found, should the bank de-anonymize the data an identify the actual account holder. (We understand this might need much more detailed explanation, rest assured we will be writing a longer post on the impact on AML/CFT processes)
- Credit Risk monitoring: Unless the risk is large it might be very difficult to justify reading of transactions. The Financial Institution will have to provide the borrower a mechanism to provide consent each time such an assessment is made. This might defeat the whole purpose as someone with a risk may actually deny consent every-time. Thus it would be interesting to see how this part of the system pans out and what regulations are framed to balance risk and privacy concerns.
Banking Agents
- Collection of data: Even current regulations require Banks to ensure that agents are registered and a clear trail can be established which ensure zero data leakage. This might now fall under a clear law or regulation, further not only Banks but all financial institutions (FIs) might need to have stricter regulations for agent models.
- Storage of data: The storage of data will strictly require physical or digital records to be destroyed by the agents post transaction. Unless there is explicit consent by the consumer for such storage.
- Sharing of data with other parties: Many a times agents do end up sharing data with parties who at the time of consent were not in the picture. As an example if the intended Bank doesn’t give a loan, data might be shared with other parties as well. Now one will need to take clear consent to ensure that this sharing is agreed by the user.
Payments
- Aadhar Pay: Biometric has been considered by the court as a core private space. And it has also opined that at times consent may not be enough as the users may not understand the risks. In this light, Aadhar Pay might not have “proportionate” good. As while KYC carries risk to financial system and hence proportionate good, mere payments might not be an ideal scenario to invade individual privacy.
- Cards based payments: Current cards eco-system relies on a “card” and PIN and no specific private data, at least from our point of view it doesn’t encroach privacy during payments. Fraud rules are also generally based on aggregated behavior and hence might also not carry any risk of privacy encroachment.
- Mobile wallets: Since it is based on a standalone wallet that I recharge it has no personal data about me other than my basic KYC, phone number, email and my transaction details. Therefore no private information is shared with wallets. But wallets would not be able to leverage on my digital footprint for credit assessment without clear consent.
Social behavioral data
- Social media: Google and Facebook have recently shown interest in using customer data gathered over a period of time as credit decision tools. This data has clearly been stated to be private. Thus this too would fall under the gambit of future regulation
- Application’s own data: Even if the data is not coming from a third party but reflects user behavior on the same platform, such as Amazon, Uber etc. It will still be considered within the domain of privacy and needs to be regulated
As social behavior data is rich and possibly being seen as an alternative to many traditional data stores it important to share another case regarding Whatsapp’s decision to share its data with Facebook (its parent company). The matter concerns the privacy of 160 million Indian Whatsapp users. Such data has expressedly been considered to be private — and Judge’s comments left no room for imagining what their views were:
“Recently, it was pointed out that “‘Uber’, the world’s largest taxi company, owns no vehicles. ‘Facebook’, the world’s most popular media owner, creates no content. ‘Alibaba’, the most valuable retailer, has no inventory. And ‘Airbnb’, the world’s largest accommodation provider, owns no real estate. Something interesting is happening. […]
Uber’ knows our whereabouts and the places we frequent. ‘Facebook’ at the least, knows who we are friends with. ‘Alibaba’ knows our shopping habits. ‘Airbnb’ knows where we are travelling to.
Social networks providers, search engines, e-mail service providers, messaging applications are all further examples of non-state actors that have extensive knowledge of our movements, financial transactions, conversations — both personal and professional, health, mental state, interest, travel locations, fares and shopping habits […]
Large number of people would like to keep such search history private, but it rarely remains private, and is collected, sold and analysed for purposes such as targeted advertising[…]
Thus, there is an unprecedented need for regulation regarding the extent to which such information can be stored, processed and used by non-state actors. There is also a need for protection of such information from the State”
These are just some of the instances that maybe impacted by this judgement. We will be happy if you can share any areas we may have missed and we will add them here.
Way Forward
This is certainly a landmark judgement and in some ways can claim to be the re-birth of privacy. In a digital world it was assumed that privacy has been sacrificed at the altar of convenience. But the court has upheld an individual’s right to his privacy providing him means to protect it and hence re-introduced a principle which seemed lost in the digital world. As the next steps, it’s incumbent upon the legislature to create clear law regarding this concern. But it’s safe to assume that usage of such data would be become much more regulated than it is now.
We are hoping that this article would be useful to you and also help you make sound business decisions. We might not have been able to go into depths of few topics which need much more deliberation. Hence we would be coming up with few more articles going in depth into some of these topics. We will be happy to receive feedback and also get to know which areas would you want much more in-depth analysis.
About Signzy
Signzy is a market-leading platform redefining the speed, accuracy, and experience of how financial institutions are onboarding customers and businesses – using the digital medium. The company’s award-winning no-code GO platform delivers seamless, end-to-end, and multi-channel onboarding journeys while offering customizable workflows. In addition, it gives these players access to an aggregated marketplace of 240+ bespoke APIs that can be easily added to any workflow with simple widgets.
Signzy is enabling ten million+ end customer and business onboarding every month at a success rate of 99% while reducing the speed to market from 6 months to 3-4 weeks. It works with over 240+ FIs globally, including the 4 largest banks in India, a Top 3 acquiring Bank in the US, and has a robust global partnership with Mastercard and Microsoft. The company’s product team is based out of Bengaluru and has a strong presence in Mumbai, New York, and Dubai.
Visit www.signzy.com for more information about us.
You can reach out to our team at reachout@signzy.com
Written By:
Signzy
Written by an insightful Signzian intent on learning and sharing knowledge.



